Reverse DNS, also known as rDNS, is a system that maps an IP address to a hostname. Unlike traditional DNS (Domain Name System), which maps a hostname to an IP address, rDNS performs the reverse process, providing an extra layer of information about the owner and location of a particular IP address.
In this article, you will understand reverse DNS records, and why it is useful.
Why Does Reverse DNS Matter?
A reverse DNS record plays an important role in email delivery, security, network management, and many others:
- Email delivery:
Reverse DNS is an important aspect of email delivery as it helps identify the source of an email message. If an email server does not have a properly configured reverse DNS, it may be marked as spam or rejected by the recipient’s email server.
- Network security:
Reverse DNS can also play a crucial role in network security. By providing information about the owner and location of an IP address, rDNS can help identify suspicious or malicious activity.
- Network management:
Reverse DNS can also help network administrators manage their networks more effectively. By providing information about the hostname associated with an IP address, network administrators can easily identify and troubleshoot network issues.
How Does Reverse DNS Work?
Reverse DNS works by using a special type of DNS record, known as a PTR (pointer) record, which maps an IP address to a hostname. When a user requests information about an IP address, the request is sent to the appropriate rDNS server, which then returns the associated hostname.
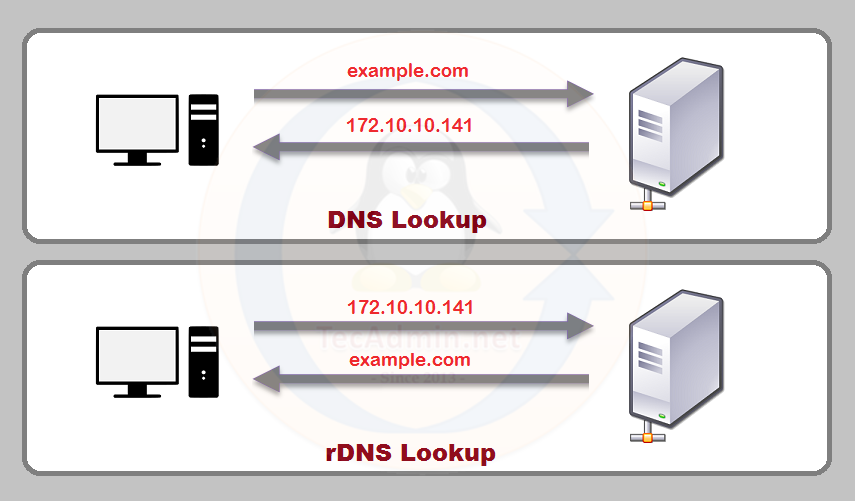
In order to use reverse DNS, a network administrator must first create a PTR record for each IP address on their network. This is typically done by contacting the organization responsible for the IP address block (known as the IP address registrar) and requesting that they create the PTR record.
How to Query Reverse DNS?
nslookup and dig are two common command-line tools that can be used to query reverse DNS records. Here’s how to use them:
- Using nslookup:
Open a Command Prompt or Terminal window and type the following command:
1nslookup -a [IP address] [DNS server]Replace [IP address] with the IP address you want to query, and [DNS server] with the DNS server you want to use (e.g., 8.8.8.8 for Google’s public DNS server)
nslookup -a 172.10.10.141The output will display the hostname associated with the IP address, as well as other information such as the authoritative name server and the time to live (TTL) of the record
- Using dig:
Open a Command Prompt or Terminal window and type the following command:
1dig -x [IP address] +short @[DNS server]Replace [IP address] with the IP address you want to query, and [DNS server] with the DNS server you want to use
dig -x 172.10.10.141 +short @8.8.8.8The output will display the hostname associated with the IP address, in a condensed format
Both nslookup and dig are powerful tools for querying DNS records, including reverse DNS records. By using these tools, network administrators can quickly and easily verify the configuration of their reverse DNS records and troubleshoot any issues that may arise.
Conclusion
In conclusion, reverse DNS is an important aspect of modern networking that provides valuable information about the owner and location of IP addresses. By facilitating email delivery, enhancing network security, and improving network management, reverse DNS plays a critical role in the functioning of today’s connected world.
