In the realm of cybersecurity and network communication, few protocols are as universally adopted as Secure Shell (SSH). Originating from the need for a secure means of remote access, SSH has been a mainstay of modern network architecture for more than two decades. But what is SSH, and how does it operate to ensure secure, encrypted networking? Let’s dive in.
What is Secure Shell (SSH)?
Secure Shell, or SSH, is a cryptographic network protocol that allows for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers. SSH is widely used by network administrators for managing systems and applications remotely, thereby enabling them to log into another computer over a network, execute commands, and move files from one machine to another.
SSH was developed as a secure replacement for less secure access protocols like Telnet, rlogin, and FTP, which send information, notably passwords, in plain text, leaving them exposed to interception. SSH, on the other hand, uses encryption to secure the connection between the client and the server, making it far more difficult for potential attackers to gain access to sensitive data.
The Architecture of SSH
SSH operates in a client-server model. The SSH server is the endpoint that accepts SSH connections from clients, and the SSH client is the application that initiates SSH connections to the server. Once the server accepts a client’s connection request, the two parties establish a secure, encrypted connection.
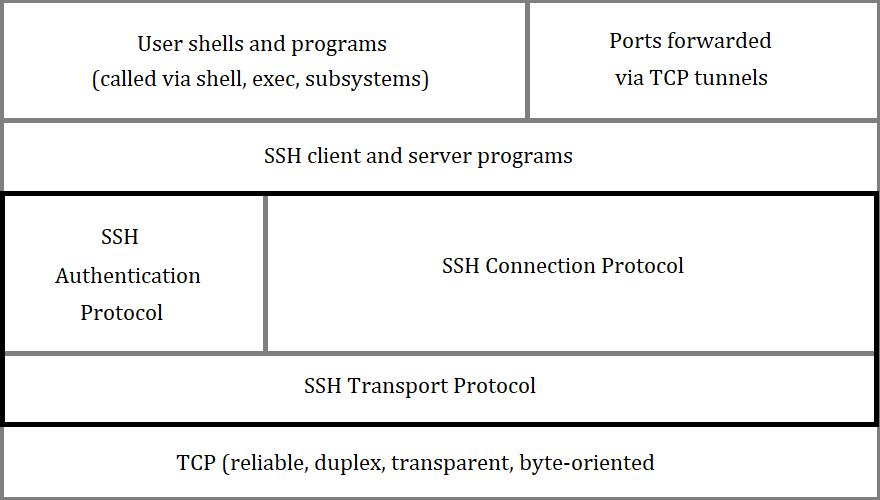
The SSH protocol is layered and consists of three main components:
- Transport Layer Protocol: This protocol provides server authentication, confidentiality, and integrity. It may optionally provide compression. It typically uses TCP/IP and provides a secure, low-level data transfer service for the client-server interaction.
- User Authentication Protocol: This protocol authenticates the client to the server. It works over the secure transport layer protocol. The client starts by sending a service request to which the server responds with a list of supported authentication methods. The client then attempts to authenticate using these methods, which could include password, public key, or others.
- Connection Protocol: This protocol multiplexes the encrypted tunnel into several logical channels. After successful authentication, the client can open multiple independent channels over the single SSH connection, allowing for a variety of services (like a terminal session, file transfers, or forwarding ports) to be used simultaneously.
Encryption and Keys in SSH
The basis of SSH’s security is its use of encryption, and the heart of this encryption process lies in SSH keys. An SSH key pair consists of two cryptographic keys: a private key that remains securely with the user, and a public key that can be shared freely with any SSH server the user wishes to communicate with.
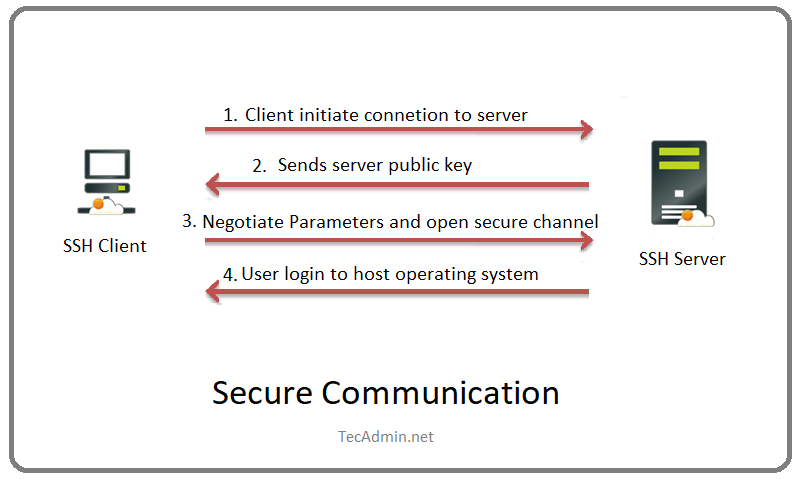
During an SSH session, these keys work together to verify identity (authentication) and to encrypt the communication (ensuring confidentiality and integrity). The SSH client initiates the process by sending the server the user’s public key. If the server recognizes the public key, an encrypted session is initiated using both the public and private keys, ensuring only the intended recipient can decipher the messages.
You may like:
The Importance of SSH
SSH plays a critical role in modern network architecture and cybersecurity. It provides a secure way to access network resources and perform administrative tasks in a distributed environment, reducing the risk of security breaches. However, like all tools, it’s essential to use it correctly. Poorly managed SSH keys, for instance, can pose a significant security risk, which is why organizations must ensure proper SSH key management.
Wrap Up
Secure Shell (SSH) is an indispensable protocol in today’s interconnected world, providing secure, encrypted network services. Its robust architecture and use of encryption make it an essential tool in the cybersecurity toolbox.

