In the ever-evolving landscape of network security, keeping your systems updated and secure is paramount. Transport Layer Security (TLS) is a critical component of secure network communication, and TLS 1.2 is the preferred version for modern security standards. This article provides a comprehensive guide on enabling TLS 1.2 on Windows Server, ensuring your system’s security is up-to-date.
Understanding TLS 1.2
TLS 1.2 is an improved version of the TLS protocol, offering enhanced security features. It addresses vulnerabilities present in earlier versions and supports stronger encryption algorithms, making it an essential update for any Windows Server environment.
Prerequisites
- A Windows Server environment (2008 R2 and later).
- Administrative access to the server.
- Basic understanding of Windows Server and networking concepts.
Step 1: Backup Current Registry Settings
We strongly recommend taking a backup of the registry before making any changes. Use below link to find steps to how to export registry values.
Step 2: Enable TLS 1.2 on Windows
You have two options to enable TLS version on your system.
Option 1: Merge Registry File
Download the Enable-TLS12-Windows.reg and Enable-TLS12-TLS11-Windows.reg files on your Windows system. Now right click on file and click Merge.
Option 2: Manually Update Registry
You can do this by directly editing registry file manually.
2.1 Open registry on your server by running ‘
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
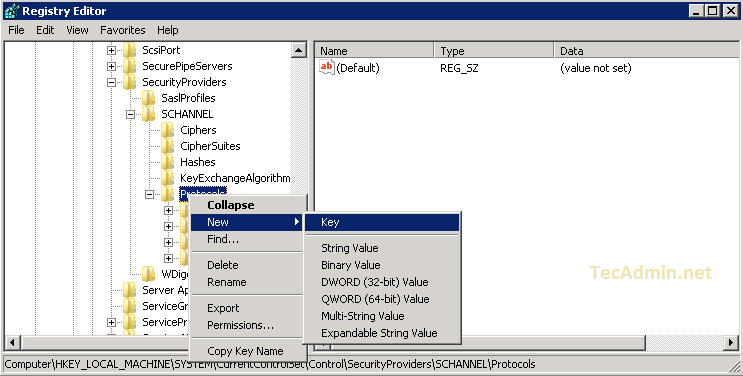
2.2 Add the TLS 1.1 and TLS 1.2 keys under Protocols. It will looks like directories.
2.3 Now create two keys Client and Server under both TLS keys.
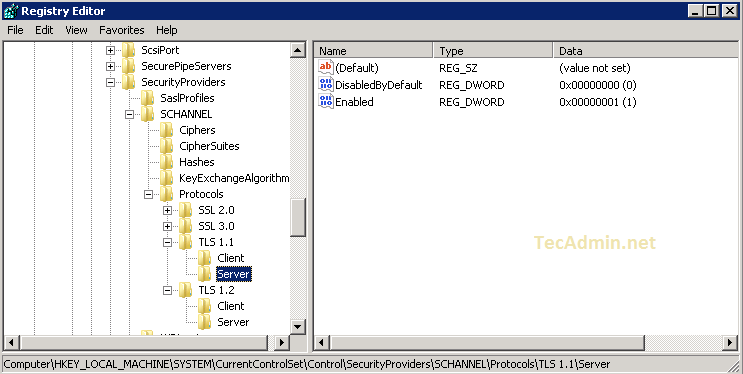
2.4 Now create the DWORD Values under Server and Client key as following
DisabledByDefault [Value = 0] Enabled [Value = 1]
Step 3: Disable TLS and SSL Older Versions
3.1 Open registry on your server by running ‘regedit’ in run window and navigate to below location.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
3.2 Now change DWORD Values under Server and Client under TLS 1.0, SSL 3.0 and Older SSL version keys.
DisabledByDefault [Value = 0] Enabled [Value = 0]
Step 4: Configuring Cipher Suites
- Determine Supported Cipher Suites: Research and select the appropriate cipher suites for your environment.
- Configure via Group Policy Editor:
- Open Group Policy Editor.
- Navigate to Computer Configuration >> Administrative Templates >> Network >> SSL Configuration Settings.
- Modify SSL Cipher Suite Order as per your requirements.
Step 5: Testing and Verification
- Restart the Server: Ensure all changes are applied.
- Verify TLS 1.2 Activation: Use a network analysis tool or PowerShell to check that TLS 1.2 is active and being used for connections.
Conclusion
Enabling TLS 1.2 on Windows Server is a crucial step in bolstering your network’s security. By following these steps, administrators can ensure that their servers are using modern, secure protocols, thereby reducing the risk of data breaches and cyber attacks. Regularly updating security protocols and staying informed about the latest in network security will further strengthen your defenses against emerging threats.

27 Comments
TC: See the following to get A+ on Windows Server 2008 R2 SP1:
1. https://www.hass.de/content/setup-microsoft-windows-or-iis-ssl-perfect-forward-secrecy-and-tls-12
2. https://support.microsoft.com/kb/3080079 <– for RDP to work with TLS 1.0 disabled
3. https://support.microsoft.com/kb/3140245 <– for WinHttp
4. https://support.microsoft.com/kb/2992611 <– for TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
5. https://support.microsoft.com/kb/3175024 <– for Diffie-Hellman ServerMinKeyBitLength
You need to install the patches per KB (items 2-5) for the registry changes (in item 1) to work.
Can’t get this working on Server 2008 R2.
Have tried manually, scripted and using Nartac’s IISCrypto, but even after a reboot, my SSL Report fails with “Assessment failed: No secure protocols supported” and I can’t connect to any of the web pages on the server.
Have repeatedly checked the registry keys so that SSL 2.0, SSL 3.0 and TLS 1.0 are disabled, TLS 1.1 and TLS 1.2 are enabled.
I noticed when I used IISCrypto though, that the values for TLS1.1 and TLS1.2 wehere configured as hex 0xffffffff or decimal value 4294967295. It is not configured as 1 as per my registry values:
*****************************************************************************************************
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Client]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Server]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
“Enabled”=dword:ffffffff
“DisabledByDefault”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
“Enabled”=dword:ffffffff
“DisabledByDefault”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
“Enabled”=dword:ffffffff
“DisabledByDefault”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
“Enabled”=dword:ffffffff
“DisabledByDefault”=dword:00000000
*****************************************************************************************************
I’m guessing the value just needs to be a positive integer. But configuring the “Enabled” DWORD as decimal 1 didn’t make any difference anyway. Trying to figure out why it’s not working though. Any thoughts?
Can you try the steps from 5-7 listed on this page
https://support.solarwinds.com/SuccessCenter/s/article/Enable-TLS-1-2-on-Windows-Server-2008?language=en_US
Thank you very much, it worked just fine in my environment (Server 2008 R2 SPK1) IIS 6.1
Thank you!
Microsoft’s official article and “easy fix” was missing some registry entries ?♂️
¡Excelente! Funcionó al 100% a la primera.
Gracias por compartir.
Worked like a champ. Thank YOU!
Here’s a PowerShell script I wrote that does it too.
$SSLTLS = “HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols”
$Types = “Client” , “Server”
$SK2V = ( 0..7 | % { 0 } ) + ( 8..9 | % { 1 } )
$Protocols = @( 2..3 | % { “SSL $_.0” } ) + @( 0..2 | % { “TLS 1.$_” } )
$Protocols | % `
{
$Path = “$SSLTLS\$_”
If ( ( Test-Path $Path ) -ne $True ) { NI -Path “$SSLTLS” -Name “$_” }
$Types | % { If ( ( Test-Path “$Path\$_” ) -ne $True ) { NI -Path “$Path” -Name “$_” } }
}
$Path = @( $Protocols | % { “$SSLTLS\$_\Client” ; “$SSLTLS\$_\Server” } )
0..( $Path.Count – 1 ) | % `
{
If ( ( gci $Path ) -eq $Null )
{ SP -Path ( $Path[$_] ) -Name “DisabledByDefault” -Type “DWORD” -Value “0”
SP -Path ( $Path[$_] ) -Name “Enabled” -Type “DWORD” -Value ( $SK2V[$_] ) } }
Please dont provide a false information on something that you are not sure about !
It’s clearly say set a dward to 1 per MS docs
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn786418(v=ws.11)#BKMK_SchannelTR_TLS12
Also there is another URL that show to how disable all the protocols on
https://support.microsoft.com/en-us/help/187498/how-to-disable-pct-1-0-ssl-2-0-ssl-3-0-or-tls-1-0-in-internet-informat
I’m shocked of the number of people who are trying to figure out things by them self ! Anyway, i will sum all that text with the registry file below:
pastebin Link : https://pastebin.com/7RN6m15G
;Start Registry File
;———————-
Windows Registry Editor Version 5.00
;Microsoft Document https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn786418(v=ws.11)#BKMK_SchannelTR_TLS12
;This document will disable the follow:
; – PCT 1.0
; – SSL 2.0
; – SSL 3.0
; – TLS 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
;PCT 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;SSL 2.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;SSL 3.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;TLS 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;TLS 1.1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
;TLS 1.2
;Note: For Win7 / Win2008R2, you must have DisabledByDefault set to 0 in client Win7 and in Both Win2008R2
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
;———————
;End Registry File
SSL Certificate Incorrect Configuration – INTG Server Accepts SYST client Certificate and returns 200 response
We have developed a Web API application and we are using Mutual TLS V1.2 for Authentication. We have two servers (X and Y) in INTG Environment and also we have a load balancer. Server X and Y are accessed via load balancer server.
I have hit one of the Web Api Get request URL by selecting the Client certificate in Chrome browser if the request goes to server Y and if I pass a valid INTG client certificate it’s working fine and If I pass invalid client certificate or other environment(SYST) certificate it throws 401 UnAuthorized. This is the correct behavior and it is working fine in Y.
But in the Server X if I pass invalid certificate it’s throwing 401 Unauthorized but if I pass SYST Client Certificate it’s working and I am getting the 200 response. It should not accept SYST client certificate in INTG Environment and it should throw 401 UnAuthorized but it is accepting it and I am getting 200 Response.
I verified both the server configurations everything appears same and I don’t see any difference.
I identified this issue by stopping the site alternatively in both the servers.
We are using “iisClientCertificateAuthenticationMapping” and in that we have set the “manyToOneCertificateMappingsEnabled” as False and “oneToOneCertificateMapingsEnabled” as True and for “oneToOneMappings” I have set the userName, password and certificate(base64string).
Can you guys please let me know what are the possible reasons for the X server’s incorrect behavior.
INTG SERVERS:
Server X
Server Y
The notion that setting the Enable key to 0x00000001 is absolutely incorrect. To activate the TLS setting, the Enable key must be set to 0xffffffff. This is the only way I could get it to function correctly
Please dont provide a false information on something that you are not sure about !
It’s clearly say set a dward to 1 per MS docs
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn786418(v=ws.11)#BKMK_SchannelTR_TLS12
Also there is another URL that show to how disable all the protocols on
https://support.microsoft.com/en-us/help/187498/how-to-disable-pct-1-0-ssl-2-0-ssl-3-0-or-tls-1-0-in-internet-informat
I’m shocked of the number of people who are trying to figure out things by them self ! Anyway, i will sum all that text with the registry file below:
pastebin Link : https://pastebin.com/7RN6m15G
;Start Registry File
;———————-
Windows Registry Editor Version 5.00
;Microsoft Document https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn786418(v=ws.11)#BKMK_SchannelTR_TLS12
;This document will disable the follow:
; – PCT 1.0
; – SSL 2.0
; – SSL 3.0
; – TLS 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols]
;PCT 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;SSL 2.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;SSL 3.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;TLS 1.0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
;TLS 1.1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
;TLS 1.2
;Note: For Win7 / Win2008R2, you must have DisabledByDefault set to 0 in client Win7 and in Both Win2008R2
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
;———————
;End Registry File
I have did exactly same on windows 2008R2 SP1 but to my surprise when i run wireshark logs i can see the communication still happens on tls 1.0. Why is it so ?
I am running Server 21012R2, and made all the suggested changes. Still, I get the handshake error when using Chrome. Is there anything else that must be done, downloaded, upgraded, whatever, to make Chrome work again?
If, like me, after making the suggested registry edits, you continue to receive the handshake fallback error, this might help:
https://support.microsoft.com/en-us/kb/2992611
This is an update that came out in 2014, but had not been installed on my server. It is a fix to a vulnerability in SChannel. After installation, Chrome displays my site properly.
Ugo Meex, you have made my day! This is the official Golden TIP of the month! Took me 4 days to investigate why Windows 10 1511 (fall update) clients couldn’t connect to our RADIUS Wi-Fi network anymore. With your tool, it took me 3 mouse clicks and 1 reboot…. everything solved.
It should be made very clear that this works for Server 2008 R2 and later, but *will not* work for “Server 2008” (which also means, it will not work for SBS 2008 either). Unfortunately, the article title is misleading; TLS 1.1/1.2 are not supported prior to Server 2008R2 and SBS 2011 on the server side.
While this article is certainly very useful, in a windows environment it would be far easier to use the IISCrypto tool by Nartac Software. It’s small, it’s free, it’s easy to use.
Rather than having to read and edit the registry, this utility gives you a GUI to make these changes.
It also offers 1 click config for: Best practices, PCI and FIPS 140-2
https://www.nartac.com/Products/IISCrypto/
Same result, but faster and certainly easier. 🙂
These instructions have been tested as incomplete… They do not disable the protocols properly… We’ve used the following script to resolve the issue successfully…
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocols]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Client]
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Server]
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server]
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client]
“Enabled”=dword:00000001
“DisabledByDefault”=dword:00000000
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server]
“DisabledByDefault”=dword:00000000
“Enabled”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0]
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Client]
“Enabled”=dword:00000000
“DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
Your script does the exact same thing as the manual instructions listed in this article, how is it incomplete?
for ssl 2.0 you have DisabledByDefault [Value = 0] but the script does “DisabledByDefault”=dword:00000001
I ran this script and it did nothing. I have Server 2008 R2. FYI, I do not have TSL 1.0 and 2.0 but if I am not wrong this script should create entries for these.
Thanks
This will not work on Windows Server 2008 SP2 but does work on Windows Server 2008 R2.
TLS 1.1 and TLS 1.2 does not seem to come with Windows Server 2008 SP2, a bit of an issue for me.
Hi Rahul, thanks for this. Shouldn’t your Step 3.2 be: DisabledByDefault [Value = 1] rather than [Value = 0] to disable by default?
Greg,
No. By setting the value of DisabledByDefault to 1, you are making the value true, thus disabling the protocol “by default”.
Isn’t disabling the SSL protocols by default exactly what is wanted?
Will this instruction to add TLS 1.1 and TLS 1.2 work on Windows 2008 Standard version?