Pip is a package installation tool that is used to get packages from the Python Package Index and various repositories. Pip, which stands for “Preferred Installer Program”, is a Python-based package management application that streamlines the package installation and management process. Pip is a multi-platform package manager for Python projects which assists in managing libraries and dependencies. Pip installation on Ubuntu Linux is a quick and straightforward procedure. The latest Python 3 is included in the standard system installation starting with Ubuntu 20.04. The source code for Python 2 may be found in the general source repository. However, users are…
Author: Rahul
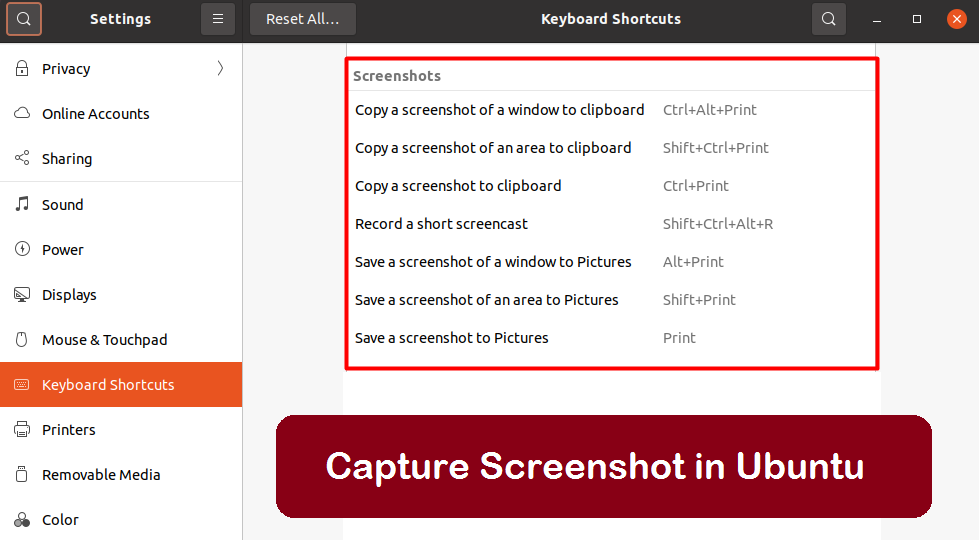
Ubuntu is one of the most popular Linux distributions in the world, offering a reliable and user-friendly operating system for a variety of users. Whether you’re a developer, a student, or just someone who wants to use a free and open-source alternative to Windows or macOS, Ubuntu is a great choice. One common task that users often need to perform on their Ubuntu machines is capturing screenshots. Whether you’re taking screenshots for documentation purposes, sharing information with colleagues or friends, or just capturing an interesting moment on your screen, there are several easy ways to capture screenshots in Ubuntu. In…
In certain situations, you may want to remove a file from your Git repository but keep the local copy of the file. This could be useful when dealing with sensitive information, large files, or configuration files that need to be customized per user. In this article, we will walk you through the process of removing a file from your Git repository while keeping the local version intact. Step 1: Open the terminal Begin by opening your terminal window. You can use the default terminal application for your operating system or any other terminal emulator you prefer. Step 2: Navigate to…
PostgreSQL is an advanced, open-source relational database management system. It is written in C programming language and was developed at the University of California, Berkeley in 1996. Initially, version 1.0 of Postgres95 was announced on September 5, 1995. The first non-university version of PostgreSQL was provided on July 8, 1996, by Marc Fournier at Hub.org Networking Services. Which is the first version of PostgreSQL for public use. As of today, PostgreSQL 13.3 is the latest stable version available for installation. PostgreSQL version 9.5 and lower versions are no more supported by the team. In this tutorial, you will learn, how…
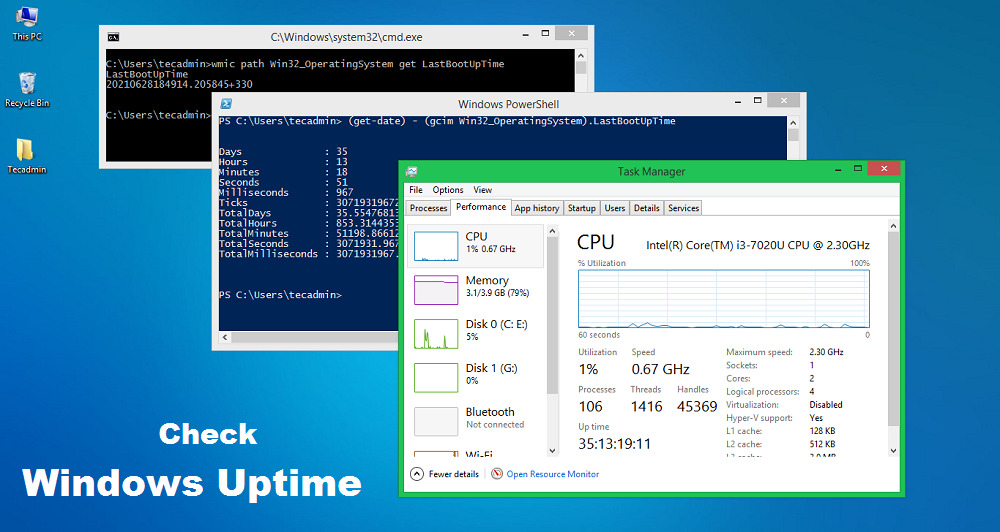
Computer Uptime refers to how long a system has been up and running without any shutdown or restart. The computer uptime helps us to find the last reboot of any system. This can be helpful in many ways like troubleshooting or scripting etc. In this tutorial, we will discuss three ways to check the uptime of any Windows machine or server. 1. How to Check Windows Uptime with Task Manager A task manager is a computer program used for checking the process and services running and their details. You can also find details about the resource utilization like Memory and…
As more and more of our lives move online, it’s becoming increasingly important to protect our online privacy and security. One way to do this is through the use of SSH tunneling, a method of encrypting your internet traffic to keep it safe from prying eyes. In this beginner’s guide, we’ll explain what SSH tunneling is, how it works, and how you can set it up. What is SSH Tunneling? SSH (Secure Shell) is a network protocol that allows you to securely access and control a remote computer. SSH tunneling, also known as SSH port forwarding, is a technique that…
There are thousands of Linux distributions available that you can use. However, people can’t choose one perfect OS that they can use as an alternative to Windows 10 or 8. Now, when it comes to Windows, it’s pretty easy to use. The same isn’t applicable for Linux. Here, you will have to need basic knowledge to operate and use the operating system. Therefore, people often choose the Linux distribution that is easy to use for a Windows user. 10 Best Linux Server Distributions 10 Best Linux Desktop Distributions 5 Best Linux Distributions that Looks Like MacOS 5 Most Stable Linux…
Secure Shell (SSH) is one of the most commonly used and secured ways to connect to a remote server. It is easy to connect with a remote server with SSH but what if you want to connect with different servers and you do it frequently. It becomes difficult to remember all the IPs addresses, usernames, commands, and passwords. So to solve this problem, SSH allows you to set and use the ssh config file for different use-cases. SSH uses a system and custom or user-specific configuration file. You can customize and configure client-side connection options and can store information of…
While working with the databases, many times you may need to rename a database. For security purposes, MySQL had dropped the direct command to rename a database from MySQL 5.1.23. So there is no direct command to the T-SQL statement available for renaming a database in MySQL server. You can follow one of the below instructions to rename a MySQL database with the help of cPanel, phpMyAdmin, or command line as per the availability. After renaming the database, remember that you need to reconfigure the permission on the new database for the users. In this tutorial, you will find three…
When we talk about accessing servers remotely, the first thing that comes to our mind is SSH. It is a network protocol and a secured version of Telnet and encrypts the connection so others cannot access the information being transmitted. With advancements in the technology world, hackers are becoming more sophisticated every day. Even your SSH connection is not secure if you are using the traditional or default installation settings. Therefore, it has become necessary to secure your SSH server from unwanted data breaches and malicious attacks by taking some crucial precautions. In this article, we will introduce you to…