Securing your server is important to keep it safe from unwanted access. One simple way to do this is by allowing only SSH connections to your server. SSH (Secure Shell) is a secure way to connect and manage your server remotely. You can use a tool called iptables, which is like a traffic controller for your server, to block all connections except SSH. This means only people with permission can access your server using SSH, keeping it safe from others. In this guide, we’ll show you how to set up iptables to allow only SSH access, making your server more…
Author: Rahul
Handling files is a key skill in learning Linux, especially when you need to delete lines that match a certain pattern. You can do this using tools like grep, sed, and awk on the command line. In this article, we’ll show you how to use these tools to search for and remove specific lines from a file in Linux. Before you start: Always make a backup of your files before making changes. Remember, there is no ‘undo’ button in the command line, so if you delete something by mistake, you won’t be able to recover it. 1. Using grep grep…
Linux, a robust, flexible, and open-source operating system, is a favorite among many system administrators and developers due to its powerful command-line tools. One important ability of these tools is the manipulation of files, including the deletion of specific lines from a file. This article will serve as a practical guide to deleting specific lines from Linux files using different commands like sed, awk, and grep. Understanding File Line Deletion Deleting lines from files is a routine task, especially when dealing with large data or log files. It is often necessary to remove unnecessary or irrelevant data. This task can…
In this article, we will discuss multiple ways to delete the last N lines from a file in Linux. For this purpose, we will use various Linux utilities like sed, awk, and head. Before we proceed, it’s important to mention that manipulating files directly on a Linux system can potentially be destructive if not done properly. Always make sure you have a backup of your file before performing these operations, especially if the file contains important data. 1. Using the head command The head command in Linux is used to print the top N number of data of the given…
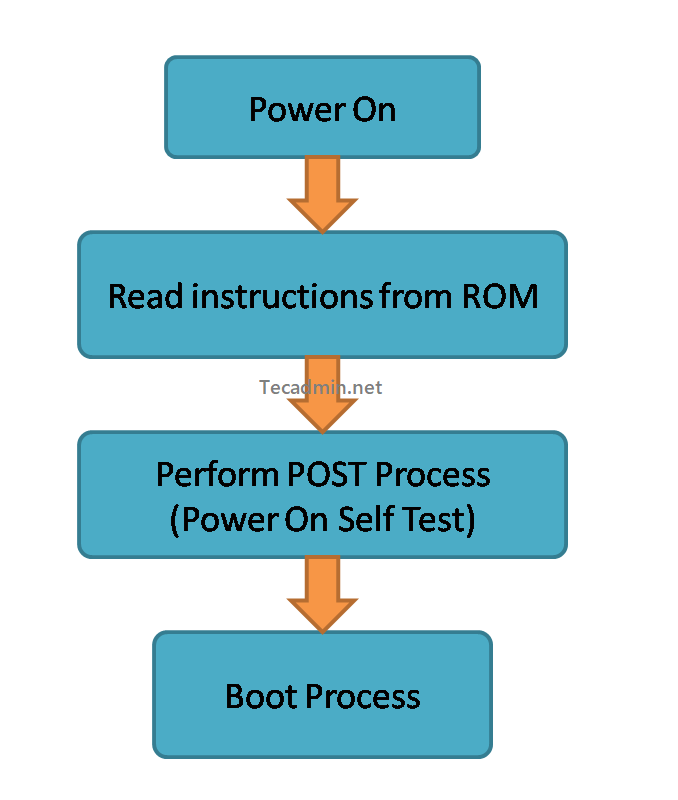
The Power-On Self-Test, commonly known as POST, is a critical part of a computer’s startup sequence. This built-in diagnostic program checks your computer’s hardware to ensure everything is functioning correctly before the operating system begins to load. What is POST? POST is a process run by firmware or software on a computer and other devices, typically as soon as the machine is powered on. The primary purpose is to test various system components and ensure they’re functioning properly before booting the main operating system. This process is executed by the system’s Basic Input/Output System (BIOS) or, in modern systems, by…
In this article, we will be exploring a common and simple problem in computer programming: finding the largest number among three given numbers. The language we will use to address this problem is C, a general-purpose, procedural computer programming language. C provides the constructs necessary to map efficiently to typical machine instructions. In other words, it is a popular language for system programming, though it is also used for a variety of other applications. Basics of the C Programming Language Before diving into the problem, let’s start with a brief introduction to the C programming language. Developed in the early…
Working with timezones is an essential part of many Python applications. Whether you’re building a scheduling system, a logging tool, or any other application that involves dates and times, setting the default timezone is a critical function. In this article, we’ll discuss how to get or set the default timezone in Python. Using the datetime Module The datetime module provides several functions for working with dates and times in Python, including setting the default timezone. To set the default timezone, you can use the tzset() function from the time module. Here’s an example code snippet that demonstrates how to set…
Understanding the function and importance of MAC addresses is essential for anyone dealing with computer networks, be it a home network or a complex business setup. This article provides a comprehensive guide on Media Access Control (MAC) addresses, their role in network communication, and their significance in today’s digital world. What is a MAC Address? A MAC address (Media Access Control address) is a globally unique identifier assigned to a network interface controller (NIC) for communications on the physical network segment. These addresses are used in most network technologies, including Ethernet, Wi-Fi, and Bluetooth. A MAC address comprises six groups…
In the world of cybersecurity, one name that invariably pops up when discussing web application vulnerabilities is Cross-Site Scripting, popularly known as XSS. A pervasive issue in internet security, XSS attacks have a significant potential for harm, primarily because they target a website’s users rather than the website itself. This article aims to delve into what XSS is, the different types it comes in, how it operates, and the potential ways to mitigate such attacks. What is Cross-Site Scripting (XSS)? Cross-Site Scripting is a type of security vulnerability typically found in web applications. XSS enables attackers to inject malicious scripts…
In the vast world of cybersecurity, Content Security Policy (CSP) serves as a formidable front-line defence. Introduced to augment the web’s native security capabilities, CSP empowers web developers to establish guidelines or “policies” that regulate how content is handled on a particular webpage. This tool aids in preventing and mitigating potential attacks, such as Cross-Site Scripting (XSS) and data injection attacks. This article offers an in-depth analysis of CSP, discussing its functions, structure, benefits, and limitations, with practical examples for enhanced understanding. Understanding Content Security Policy CSP is an HTTP response header that forms part of a multi-tiered security strategy…