One of the most powerful aspects of Linux and Unix-based systems is their command-line interface (CLI). The CLI enables users to execute tasks with an unparalleled level of precision and control. Among the many tasks that can be performed via the command line, process management is arguably one of the most crucial. Process management includes starting, stopping, suspending, and resuming processes. However, there are times when a process may not respond as expected or become resource-intensive, leading to system slowdown or even a crash. At such times, it becomes necessary to forcefully terminate or ‘kill’ the process. This article provides…
Author: Rahul
Questions:- How do I flush Postfix mail queue? How to remove emails from mail queue in Sendmail? Sendmail flush mail queue commands? Sendmail remove differed emails from the queue? Sendmail empty the mail queue command line? Sendmail is a widely-used, open-source Mail Transfer Agent (MTA) included with many Unix and Linux-based systems. Its primary purpose is to send, receive, and route emails. However, sometimes it may encounter issues that cause emails to remain queued instead of being sent out. It is therefore crucial to know how to manage and flush the mail queue when necessary. This article will walk you…
In the realm of programming, one concept that holds an indisputable significance is the concept of a ‘function’. A function can be understood as a reusable piece of code designed to perform a specific task. Functions serve as the building blocks in the structure of a program and contribute significantly to reducing code redundancy and enhancing readability. By neatly packaging code snippets into functions, developers can create modular code that’s easier to understand, debug, and manage. Functions are integral in nearly every programming language, each providing unique syntax and constructs to define and use them. However, the underlying principle remains…
In the world of macOS, there are several different ways to install software, from the Mac App Store to downloading and running .dmg packages manually. However, these methods often require lots of clicking and user interaction. If you’re someone who likes the command-line interface, or if you’re looking for a way to automate installations, Homebrew-Cask can be a great tool. Let’s dive deep into this tool and learn how to use it effectively to master your macOS experience. 1. What is Homebrew-Cask?
In the vast world of Linux, understanding how your system is using memory is a fundamental skill. This knowledge allows you to monitor the health and performance of your system, diagnose issues, and optimize resource allocation. One of the most important commands in your toolkit for this purpose is the ‘free’ command. Despite its simplicity, ‘free’ provides valuable insight into your system’s memory usage. This beginner’s guide will take you through the basics of the ‘free’ command, helping you to understand how to interpret its output. Understanding the ‘free’ Command The ‘free’ command, as the name suggests, provides information about…
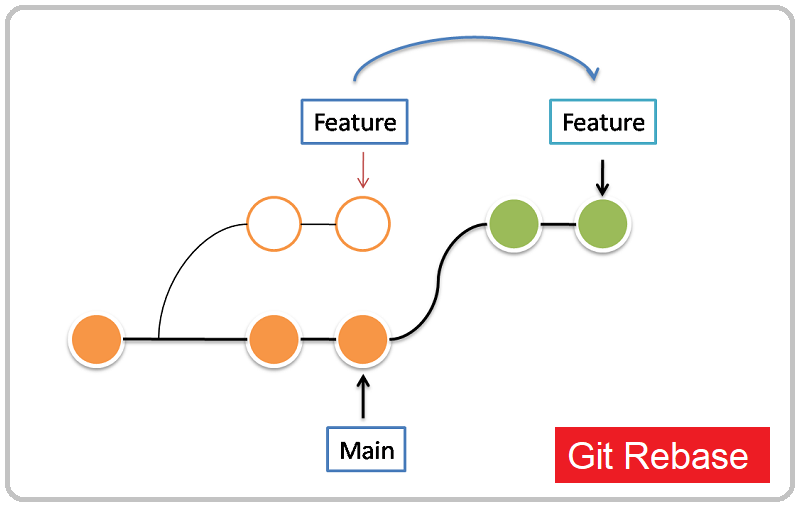
Git rebase is a powerful command that allows you to change your project history in many ways, such as editing, deleting, and squashing commits. It’s very useful for keeping a clean and readable history. However, `git rebase` can be quite complex and can have significant consequences if not used correctly. Therefore, it’s crucial to understand what each step does. This tutorial will cover the basics of `git rebase`, with the help of examples, and will show how it can be used in a workflow. What is Git Rebase? Git rebase is a command in Git, a distributed version control system.…
Git has become the de facto standard for version control and collaboration in software development. At times, developers may need to move an entire Git repository, including its history, branches, and tags, to a new location or hosting service. In this comprehensive guide, we will discuss the process of seamlessly relocating a complete Git repository without losing any crucial data or history. Preparing for the Move Before initiating the move, ensure that you have a backup of the repository, and all local changes are committed and pushed to the current remote. This step will prevent any loss of data during…
In Unix and Unix-like operating systems, the shell serves as a command-line interpreter, permitting users to issue commands that the OS will then execute. Among the most popular shell interpreters are Bourne shell (sh), Bash (Bourne Again SHell), and csh (C-shell). Shell scripts, collections of commands meant to be executed by the shell, make tasks automated and efficient. However, dealing with special characters in shell scripts can be a challenge. This article will explore how to effectively handle special characters in shell scripts. Introduction to Special Characters A special character in a shell script context is a character that has…
When it comes to shell scripting, two prominent shells often come to the fore: the Bourne Shell (SH) and the Bourne Again Shell (Bash). Both are integral components of Unix and Linux-based systems, providing an interface to interact with the operating system. This article aims to delve into the intricate differences between these two shells, unraveling their unique characteristics, and providing a comparative analysis to help you understand when and why to use one over the other. What are SH and Bash? SH, the original Bourne Shell, was introduced in the 1970s as the primary shell for Unix. Stephen Bourne…
In programming, you often find yourself working with strings of text. In Bash scripting, one common task you may encounter is the need to convert a string to lowercase. This could be necessary for reasons such as making string comparison case-insensitive or normalizing user input. In this article, we will explore different ways to convert a string to lowercase in Bash. 1. Using Bash’s Built-In Parameter Expansion Bash 4.0 and later versions have built-in string manipulation support. Parameter expansion is a powerful feature that lets you manipulate shell variables directly. To convert a string to lowercase, you can use the…