When you want to schedule jobs and programs to run automatically at certain times or when something else happens, you have many options. You can use a common tool like cron, which is built into macOS and Linux, or a special tool like AWS Lambda. Cron is not as powerful as AWS Lambda, but it works well for background tasks on Unix systems, especially if you are using containers. However, with Docker, it’s a bit more complicated because you can’t simply start a new cron job from your terminal and expect it to work. How to Dockerize a Cron Job…
Author: Rahul
Docker is a popular tool for packaging and deploying applications, and a key part of the Docker workflow is running Docker containers. In this beginner’s guide, we will explain what Docker containers are and how to run them. What is a Docker Container? A Docker container is a lightweight and standalone executable package that includes everything needed to run an application, including the code, a runtime, libraries, environment variables, and config files. Containers are built on top of Docker’s open-source containerization technology, which allows developers to package and deploy applications in a container, making it easier to run applications consistently…
If you’re a Python programmer, you may have heard of the `writelines()` Method. But what exactly is it? The `writelines()` Method is a powerful tool that makes it easy to write a list of strings to a file. You can think of it as a shortcut for writing multiple lines to a file. It’s a great way to save time and effort when writing files. The `writelines()` method in Python is a method that is used to write a list of strings to a file. It is a method of the File object in Python, which represents an open file.…
Have you ever wanted to read a file line by line in Python? Then you should be familiar with the Python `readlines()` Method! This powerful Python Method is used to read a file line by line and store each line in a list. This means you can access each line of the file using a simple list index, and you can easily manipulate the contents of the file. The `readlines()` Method is very useful for reading files that contain lots of information or have many lines of text. You can also use the `readlines()` Method to read a file one…
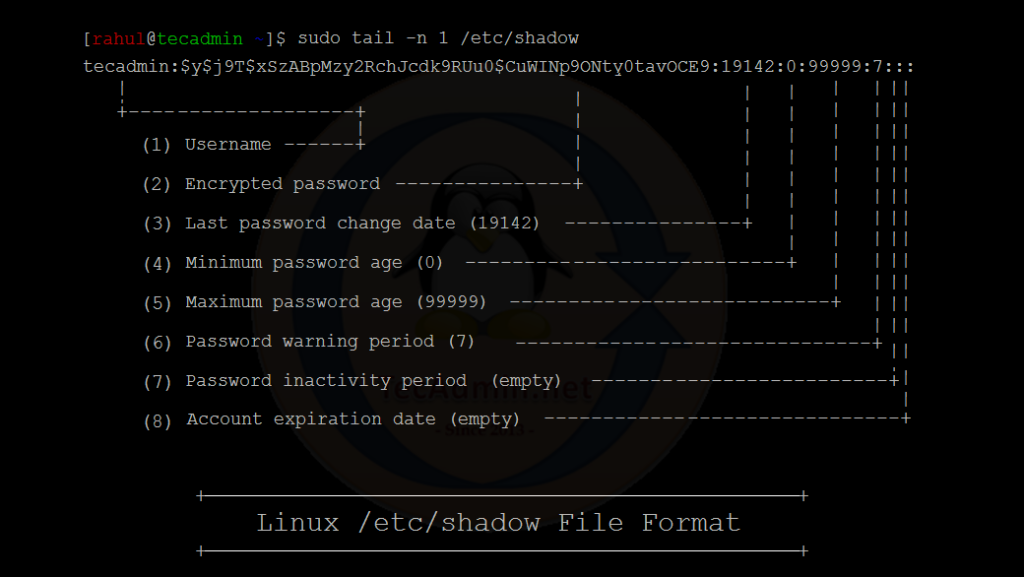
Linux-based systems, renowned for their robust security measures, segregate sensitive data to ensure minimal unauthorized access. One such piece of data is user passwords. Contrary to what some might think, these passwords aren’t stored in plain text or even in the /etc/passwd file anymore. Instead, they reside encrypted within the /etc/shadow file. This article delves deep into the structure, purpose, and utilities related to the /etc/shadow file. 1. Background and Purpose In the early days of Unix, user passwords were stored in the /etc/passwd file in an encrypted form. However, since this file had to be world-readable to allow various…
Docker is a popular tool for packaging and deploying applications in an isolated environment, and a key part of the Docker workflow is building Docker images. We can build our own images with the help of base images and use them to create containers. We can also pull the images directly from the docker hub (https://hub.docker.com/) for our application. In this beginner’s guide, we will explain what Docker images are and how to build them. What is a Docker Image? A Docker image is a lightweight, stand-alone, and executable package that includes everything needed to run a piece of software,…
Bash functions are a handy way to group a series of commands that you often use together. They allow you to reuse code, make your scripts more organized and easier to read, and save you time by not having to type out the same commands over and over again. To create a function in Bash, you use the function keyword followed by the name of the function and a pair of curly braces that enclose the commands that make up the function. For example:
1 2 3 | function greeting { echo "Hello, world!" } |
This creates a function called `greeting` that simply outputs the string “Hello, world!” when it…
While working with the Python application, you would be required to read and write text files in Python. You can refer to our other tutorial to write a text file in Python. Reading a text file in Python is a simple process that can be accomplished using a few different methods. In this article, we will cover the following methods for reading a text file in Python: Using the `open()` function and `.read()` method Using the `open()` function and `.readlines()` method Using the `with` statement and `.read()` method Using the `with` statement and `.readlines()` method You can choose anyone the…
Databases are the backbone of any data-driven application or system. They provide a systematic way to organize, retrieve, update, and manipulate data. One of the most popular databases in the world is MySQL, which is widely used for web applications and embedded database systems. Python, on the other hand, is one of the most versatile and widely used programming languages. It’s no wonder that Python and MySQL often go hand-in-hand in the development of robust applications. In this article, we are going to delve into the process of connecting Python to a MySQL database. By the end of this guide,…
In Bash, it is often necessary to check if a command succeeded or failed. For example, you may want to execute different commands based on the success or failure of a command, or you may want to perform error handling in a script. To check if a command succeeded or failed in Bash, you can examine the exit status of the command. The exit status of a command is a numerical value that indicates the success or failure of the command. A command with an exit status of 0 indicates success, and a command with a non-zero exit status indicates…