A Palindrome is a sequence that reads the same backward as forward. In the context of number theory, a palindromic number or numeral palindrome is a number that remains the same when its digits are reversed. This article aims to guide you through the process of developing a Python program that can determine whether or not a number is a palindrome. Let’s dive into the step-by-step guide. Step-by-step Guide to Create a Palindrome Checker Step 1: Take Input from the User The first step in our Python program is to take the number as input from the user. Python has…
Author: Rahul
Django, a high-level Python Web framework, promotes rapid development and clean, pragmatic design. Developed by experienced developers, it takes care of much of the hassle of web development, so you can focus on writing your app without needing to reinvent the wheel. One of the key features of Django is its automatically generated admin interface, which is highly extensible and customizable. This article provides an in-depth guide on how to create an admin user in Django using the command line interface (CLI). Activating the Virtual Environment Assuming that you already have a Django application for which you need to create…
In the world of Linux, environment variables play a crucial role in determining the behavior of various processes in the system. One such environment variable is LD_LIBRARY_PATH. This article aims to provide a comprehensive understanding of the LD_LIBRARY_PATH environment variable in Linux. We’ll discuss what it is, how it works, how to use it, and its implications on system performance and security. What is LD_LIBRARY_PATH? The LD_LIBRARY_PATH is an environment variable in Unix-like operating systems, including Linux, which is used by the system’s linker (`ld`). This environment variable specifies a list of directories where shared libraries are searched for first,…
Elasticsearch is a real-time, distributed, and scalable search engine based on Lucene, enabling users to store, search, and analyze massive volumes of data swiftly. It’s often used for log and event data analysis in IT environments. In this guide, we will explain how to install and configure Elasticsearch on Ubuntu 22.04. Please note, this guide assumes that you are working as a non-root user with sudo privileges configured on a Ubuntu 22.04 server. Step 1: Installing Java Since Elasticsearch is built using Java, we need to install it. At the time of writing, Elasticsearch requires at least Java 8 to…
The Fibonacci sequence is a series of numbers where the next number is found by adding up the two numbers before it. The sequence starts with 0 and 1. These are the first and second terms, respectively. For example, the sequence up to the 7th term is as follows: 0, 1, 1, 2, 3, 5, 8. In Python, we can implement a Fibonacci sequence using different approaches. This article will focus on two methods: generating a Fibonacci sequence up to a certain number of terms, and generating a Fibonacci sequence up to a given maximum number. 1. Fibonacci Sequence up…
The Fibonacci sequence is an interesting mathematical concept, used in various aspects of computer science, from algorithms to database systems. In this article, we will look at how you can create a Bash script to generate the Fibonacci sequence. We’ll approach this in two ways: first, generating a specific total number of elements in the sequence, and second, generating the sequence up to a given maximum number. Bash Script for Printing a Total Number of Fibonacci Numbers The first approach is to write a script that prints a set number of Fibonacci numbers. Here, the user specifies the total number…
The Fibonacci Sequence is a series of numbers in which each number (Fibonacci number) is the sum of the two preceding ones. The sequence often starts with 0 and 1. In mathematical terms, the sequence is defined by the recurrence relation: Fn = Fn-1 + Fn-2 with seed values: `F0 = 0` and `F1 = 1`. The first few Fibonacci numbers are: 0, 1, 1, 2, 3, 5, 8, 13, 21, 34, and so on. In this article, we will see how to generate Fibonacci numbers in the C programming language using two different methods. The first method will print…
As the trend toward secure web traffic continues to increase, more sites than ever are using SSL/TLS certificates to ensure secure communication between servers and clients. Among the many options for obtaining these certificates, Let’s Encrypt stands out as a reliable, free, automated, and open Certificate Authority (CA). They provide a convenient wildcard certificate, which is handy when you have a site with multiple subdomains. This article will provide a step-by-step guide on how to renew your Let’s Encrypt wildcard certificate using DNS validation. Prerequisites Before proceeding, you will need: A domain name with a wildcard certificate issued by Let’s…
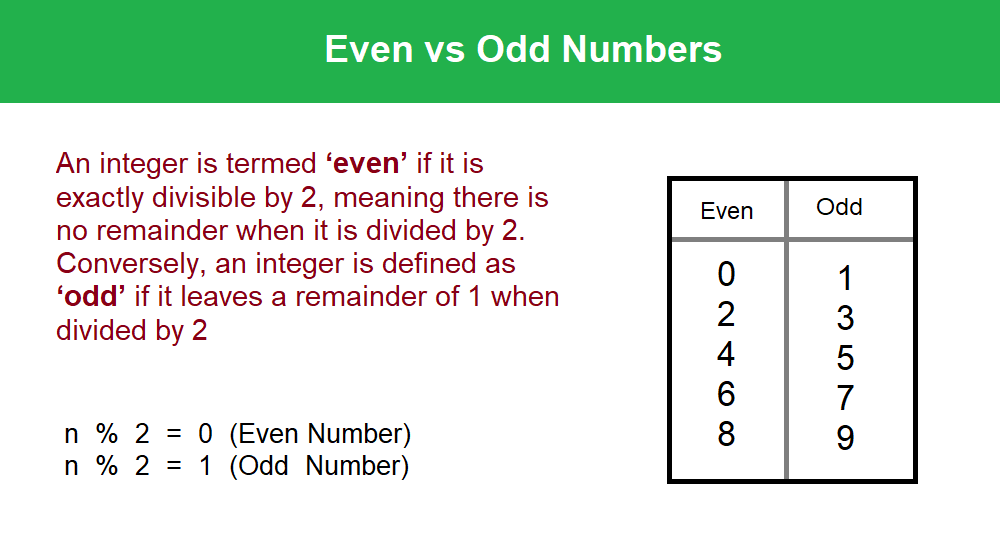
Hello friends! Today, we are going to talk about something very simple but super important in maths – even and odd numbers. Don’t worry if you’re new to this. I’ll explain it in a way that’s easy to understand, like chatting with a friend over chai! Let’s dive in. Definitions In maths, every number is either even or odd. It’s like dividing numbers into two teams. But how do we know which team a number belongs to? It’s all about whether you can divide the number by 2 or not. Let’s break it down: Even Numbers: These are numbers that…
JavaScript’s `sessionStorage` is an essential tool for managing data within a user’s browser session. It is a part of the Web Storage API that also includes `localStorage`. This guide will walk you through the usage of `sessionStorage`, its benefits, and its limitations. We will illustrate these points with clear, practical examples. What is sessionStorage? `sessionStorage` is a type of web storage that allows you to store key-value pairs in a web browser. The stored data remains intact only until the browser or tab is closed, making it an ideal choice for data that needs to persist across various pages of…