High traffic websites demand top-notch database performance to ensure fast page loads, smooth user experience, and efficient data processing. As one of the most popular open-source relational database management systems, MySQL is commonly used for powering such websites. InnoDB, MySQL’s default storage engine, is designed for high concurrency and transactional processing, making it a strong choice for high traffic websites. However, optimizing InnoDB is crucial to fully harness its capabilities and achieve the best possible performance. In this article, we will explore techniques and best practices to optimize InnoDB for high traffic websites. We will cover essential aspects of InnoDB…
Author: Rahul
MySQL is a widely-used open-source relational database management system (RDBMS) that powers numerous web applications and services. By default, MySQL stores its data in a predefined directory on Ubuntu and Debian systems, which may not always be suitable for your requirements. For instance, you might want to move the data directory to another location for better performance, security, or to utilize a separate disk or partition. In this comprehensive guide, we will walk you through the process of changing the default MySQL data directory on Ubuntu and Debian systems, ensuring a smooth transition with minimal downtime. Step 1: Preparing the…
In today’s fast-paced digital landscape, the performance of your database can have a significant impact on your application’s overall user experience and functionality. MySQL, as a robust and versatile open-source relational database management system, is a popular choice for many developers and businesses. However, as your database grows and your application scales, you may encounter slower query performance, which can ultimately affect user satisfaction and system efficiency. To ensure that your MySQL database operates at its full potential, it is crucial to employ performance tuning techniques and best practices. In this article, we will delve into ten MySQL performance tuning…
cURL (Client URL) is a versatile command-line tool that allows you to transfer data to or from a server using various protocols, such as HTTP, FTP, and many others. It is widely used by developers for testing APIs, downloading files, and automating tasks. In this tutorial, we will learn how to use cURL, a powerful command-line tool, to send raw body data to a server. This skill is essential for testing APIs, debugging server issues, or automating interactions with web services. Examples After installing cURL, you can use it to send a POST request with raw body data. We’ll discuss…
A Relational Database Management System (RDBMS) is a powerful software tool that manages and maintains structured data in an organized and efficient manner. The relational model, introduced by Dr. E.F. Codd in 1970, laid the foundation for modern database management systems. This article will provide an in-depth look at RDBMS fundamentals, including key concepts, advantages, and the various components of relational databases. Key Concepts of RDBMS Tables In RDBMS, data is organized in the form of tables, which consist of rows and columns. Each row represents a unique record or instance of data, while each column represents a specific attribute…
Python decorators are a powerful and expressive feature that allows you to modify the behavior of functions or methods in a clean and maintainable way. They can be used to perform various tasks, such as logging, memoization, and access control, without modifying the code of the decorated function. This comprehensive guide will demystify Python decorators, covering their syntax, structure, practical examples, and tips for using them effectively. What are Python Decorators? Decorators are a way to modify or extend the behavior of a function or method without changing its code. They are essentially functions that take another function as input,…
Monitoring the status of critical services running on your Linux system is essential for ensuring smooth and uninterrupted operation. One way to achieve this is by using cron jobs to periodically check the status of these services and send notifications when their status changes. In this article, we will explore how to set up a cron job to monitor the service status, and discuss different notification methods, including email, SMS, and push notifications. Overview of Cron Jobs and Service Monitoring Cron is a time-based job scheduler in Unix-like operating systems, allowing you to run scripts or commands at specified intervals.…
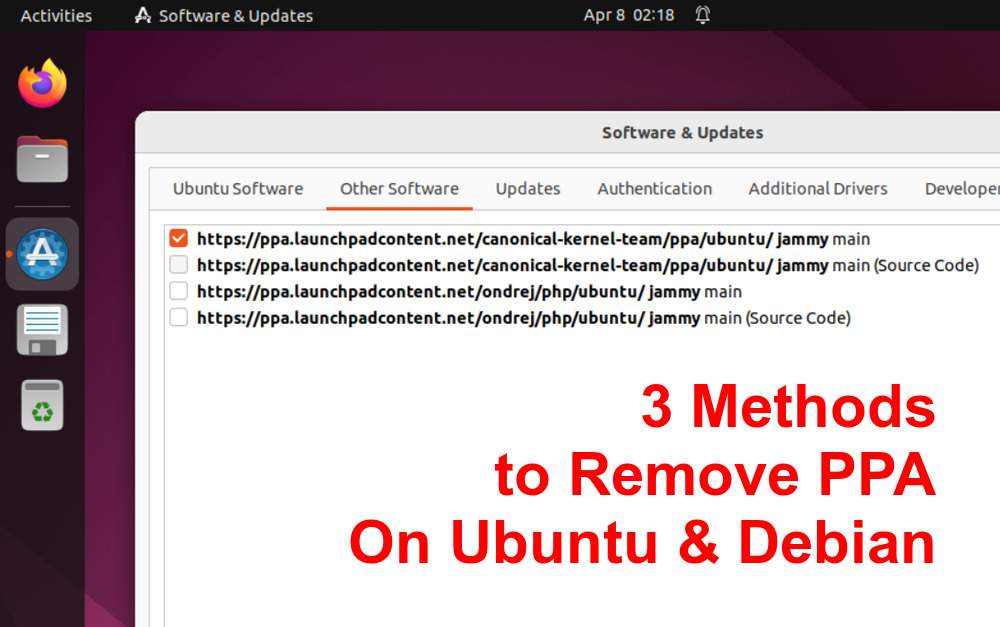
Personal Package Archives (PPAs) are a convenient way for Ubuntu and Debian users to install and update software packages that are not available in the official repositories. While PPAs are a valuable resource, they can also become outdated, unsupported, or even potentially harmful. In such cases, it’s essential to know how to remove them from your system. In this article, we’ll discuss three methods to remove PPA repositories on Ubuntu and Debian systems: using the add-apt-repository command, the ppa-purge utility, and a graphical user interface (GUI) tool. Method 1: Remove PPA using add-apt-repository command The add-apt-repository command allows you to…
Transport Layer Security (TLS) is a cryptographic protocol designed to secure communications over a computer network. TLS 1.2, released in 2008, has become the de facto standard for secure data transmission. As a .NET developer, it’s essential to understand how to implement and configure TLS 1.2 within your applications. In this tutorial, we will walk you through a step-by-step guide to securing your .NET applications with TLS 1.2. Prerequisites Before we begin, ensure you have the following: A basic understanding of .NET programming. Visual Studio installed on your computer. A .NET application in which you want to implement TLS 1.2.…
Node.js is an open-source, cross-platform runtime environment for executing JavaScript code on the server-side. Built on Chrome’s V8 JavaScript engine, Node.js allows developers to build scalable network applications with ease. This article will guide you through the process of installing Node.js on CentOS Stream 9 and RHEL 9 (Red Hat Enterprise Linux). Prerequisites A CentOS Stream 9 or RHEL 9 system with root or sudo user access. Access to a terminal or command-line interface. Step 1: Update Your System Before installing Node.js, it’s essential to ensure your system is up to date. Open your terminal and execute the following command:…