Sometimes, you might want to grant a user sudo privileges for only specific commands instead of full administrative access. This…
Browsing: Linux Security
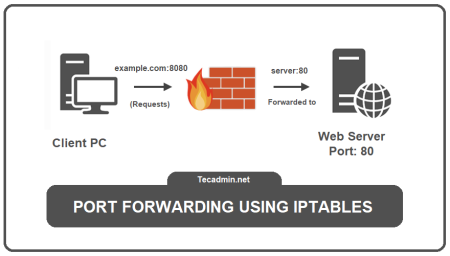
In real-life terms, Port forwarding is like telling the delivery driver where to go in a large apartment complex. Normally,…
Creating a custom script wrapper for chmod can help you manage and restrict the use of certain chmod commands, such…
In the dynamic world of network security, iptables serves as a cornerstone tool for Linux administrators. It provides powerful capabilities…
Uncomplicated Firewall (UFW) is a popular and user-friendly command-line interface designed to facilitate firewall management on Ubuntu and other Linux…
Rkhunter, short for Rootkit Hunter, is an open-source security tool that scans Linux and Unix systems for rootkits, backdoors, and…
In the realm of cybersecurity and network communication, few protocols are as universally adopted as Secure Shell (SSH). Originating from…
The SSH server has default enabled the strict host key checking. When the key checking is enabled, the SSH client…
SSH or Secure Shell is a protocol utilized to enable communication between two computers and share data. It provides a…
SELinux (Security-Enhanced Linux) is a Linux kernel security module that provides enhanced security for Linux systems. SELinux provides a mechanism…