phpMyAdmin is a popular tool used to manage MySQL databases through a web interface. However, allowing root login through phpMyAdmin…
Browsing: Security
When using keys for SSH (Secure Shell) connections, different programs often need different formats. Two common key formats are PEM…
In the ever-evolving landscape of network security, keeping your systems updated and secure is paramount. Transport Layer Security (TLS) is…
POODLE (CVE-2014-3566) is an security vulnerability in SSLv3 discovered by Google in September. POODLE stands for Padding Oracle On Downgraded…
Security of data always have in top of priorities for systems administrator’s. Systems admin’s always tries to keep all the…
We are assuming that you already have installed working Tomcat server in your system. If not you can visit to…
Malware is known as malicious software. It can be any script, app or anything which is harmful for our system…
All the sites running with SSL are used https protocol on default port 443. SSL provides secure data communication by…
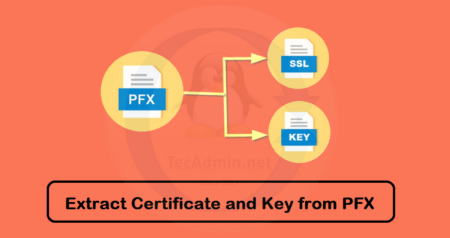
A .PFX (Personal Information Exchange) file is used to store a certificate and its private and public keys. For example,…
Fail2ban is a very useful application for you if you are managing the security of the server, or you are…