One of the most important aspects of running a Linux server is ensuring that it is secure. This means protecting against unauthorized access and preventing potential attackers from exploiting vulnerabilities in your system. One way to enhance the security of your Linux server is to disable root SSH login and create a sudo user. In this article, we’ll provide a step-by-step guide for doing just that.
Step 1: Create a Sudo User
The first step in enhancing the security of your Linux server is to create a sudo user. This user will have elevated privileges and will be able to perform administrative tasks, such as installing software and making changes to the system configuration. To create a sudo user, follow these steps:
- Log in to your Linux server as the root user.
- Use the following command to add a new user:
adduser usernameReplace “username” with the desired username for your new user.
- Set a password for the new user with the following command:
passwd username - Now, add the user in a group, that provides the sudo privilege’s. The Debain-based systems have default group name “sudo” and the RHEL-based (CentOS, Fedora, RHEL etc) have a group named “wheel”. Add the new user to the sudo group with the following commands:
- Debian-based systems:
usermod -aG sudo username - RHEL-based systems:
usermod -aG wheel username
- Debian-based systems:
- A new user account is successfully created with sudo privilege’s on Linux system
Step 2: Disable Root SSH Login
The next step in enhancing the security of your Linux server is to disable root SSH login. This will prevent anyone from logging into your server as the root user using an SSH connection. To disable root SSH login, follow these steps:
- Log in to your Linux server as the root user.
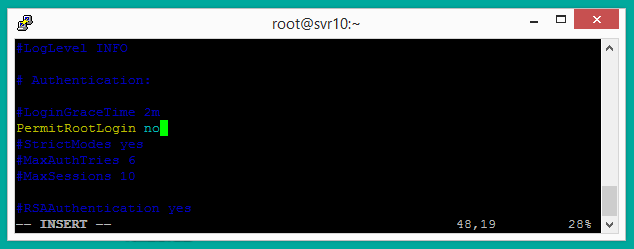
- Open the SSH configuration file with the following command:
nano /etc/ssh/sshd_config - Find the line that reads “PermitRootLogin yes” and change it to “PermitRootLogin no”.
- Save the file and close the text editor.
- Restart the SSH service with the following command:
systemctl restart ssh
Step 3: Test the Configuration
Now that you have created a sudo user and disabled root SSH login, it’s important to test the configuration to make sure everything is working as expected. To test the configuration, follow these steps:
- Log out of your Linux server.
- Log in to your Linux server as the sudo user you created in step 1.
- Use the following command to switch to the root user:
sudo su - Attempt to log in to your Linux server as the root user using an SSH connection. You should receive an error message indicating that the root login is disabled.
By following these steps, you can enhance the security of your Linux server by disabling root SSH login and creating a sudo user. This will prevent unauthorized access to your server and protect against potential attackers exploiting vulnerabilities in your system.