Linux-based systems, renowned for their robust security measures, segregate sensitive data to ensure minimal unauthorized access. One such piece of data is user passwords. Contrary to what some might think, these passwords aren’t stored in plain text or even in the /etc/passwd file anymore. Instead, they reside encrypted within the /etc/shadow file. This article delves deep into the structure, purpose, and utilities related to the /etc/shadow file.
1. Background and Purpose
In the early days of Unix, user passwords were stored in the /etc/passwd file in an encrypted form. However, since this file had to be world-readable to allow various system utilities to function, it posed a security risk. Attackers could easily copy this file and run offline password cracking attempts.
To mitigate this risk, the /etc/shadow file was introduced. This file stores encrypted user passwords in a format that is not world-readable, thus reducing the exposure of sensitive information.
2. File Structure
The /etc/shadow file consists of lines corresponding to each user account. A typical line looks something like this:
username:$6$KOhWkFd$K8B7:18333:0:99999:7:::
See the below screenshot to better upstanding:
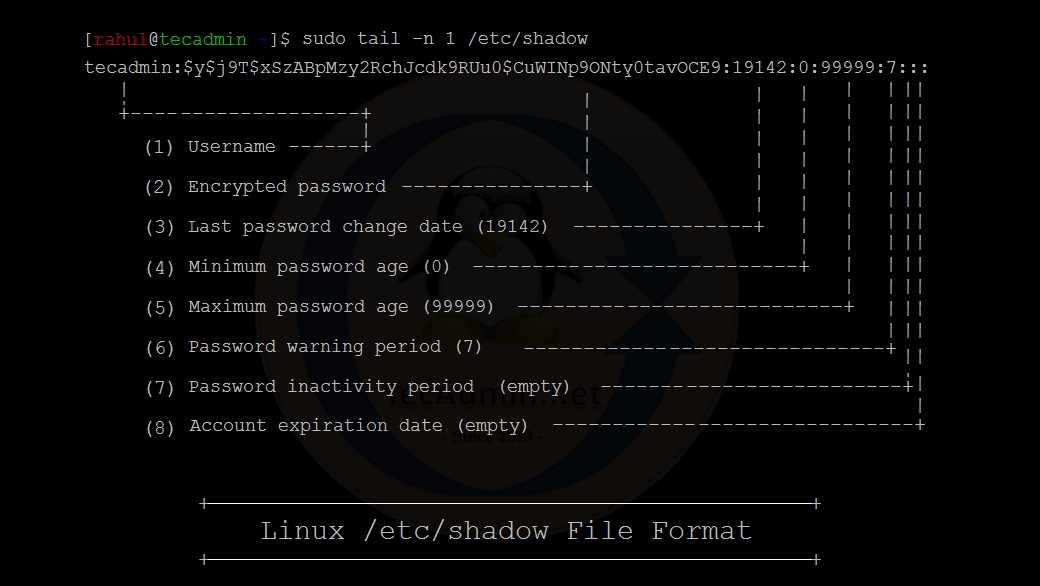
A basic overview of all the fields in the /etc/shadow file is as follows:
- Username: The name of the user account.
- Encrypted password: The encrypted password for the user account. The encrypted password is stored using a one-way hashing function, so it is not possible to retrieve the original password from the encrypted version. The initial letters of the encrypted password tell about the encryption methods used to create the password.
$1$: MD5$2a$: Blowfish$2b$: Blowfish$2y$: Blowfish$5$: SHA-256$6$: SHA-512$y$: Yescrypt
- Last password change (date): The date on which the user last changed their password, represented as the number of days since January 1, 1970.
- Minimum password age: The minimum number of days that must pass before the user is allowed to change their password again.
- Maximum password age: The maximum number of days that the user’s password is valid before it must be changed.
- Password warning period: The number of days before the user’s password is set to expire that the user will receive a warning.
- Password inactivity period: The number of days of inactivity after which the user’s password will expire and the account will be locked.
- Account expiration date: The date on which the user’s account will be disabled, represented as the number of days since January 1, 1970.
Note that the /etc/shadow file is only readable by the root user, so it is not possible for normal users to view the contents of this file or to retrieve the encrypted passwords of other users.
3. Utilities and Commands
Before we begin, it is important to note that modifying the /etc/shadow file should be done with caution, as any mistakes can potentially compromise the security of user accounts on the system. It is recommended to make a backup of the /etc/shadow file before making any changes.
- Change User Password
We can use the `passwd` command that allows us to update the password and update /etc/shadow file. For example, to change the password of your own account simply type:
passwdTo replace the password of the other user account, we can use the following command:
sudo passwd USERNAME - Setup Password Aging
Setting up password aging with the passwd command is a simple process. All you need to do is open a terminal window and type in the following command:
12## Syntaxpasswd -l USERNAME -u NUMBER_OF_DAYS -x NUMBER_OF_DAYSReplace USERNAME with the name of the user whose password you want to set up aging for. Replace NUMBER_OF_DAYS with the number of days you want the user’s password to remain valid. For example, if you want the user’s password to expire after 90 days, you would use the command:
passwd -l USERNAME -u 90 -x 7This command will set the maximum password lifetime to 90 days and the password expiration warning period to 7 days.
Once you have set up the password aging rules, you can check the status of the user’s password with the following command:
passwd -S USERNAMEThis command will give you information about the user’s password, including when it will expire and the maximum password lifetime.
4. Security Considerations
- File Permissions: By default, the /etc/shadow file has permissions set to 0400 or
-r--------. This means that only the root user can read the file, ensuring that encrypted passwords remain secure from prying eyes. - Encrypted, Not Hashed: While the term “encrypted” is commonly used, passwords in /etc/shadow are technically hashed using cryptographic hashing algorithms. This means they cannot be reversed back to plain text. The hashing algorithms (like SHA-512) are designed to be computationally intensive to fend off brute-force attacks.
- Account Locking: As mentioned, a `!` or `*` in the password field indicates that an account is locked. This is useful for creating accounts that should not be accessible by password login.
Conclusion
Understanding the /etc/shadow file is essential for anyone looking to manage or secure a Linux system effectively. This file plays a pivotal role in maintaining user authentication secrets and thus demands careful handling. By adhering to best practices and ensuring that only authorized personnel have root access, the integrity and security of a Linux system can be upheld.


