Nginx is a popular open-source web server and reverse proxy server that is widely used for serving web content and managing incoming HTTP traffic. One of the important features of Nginx is its ability to control the information that is sent to clients in the HTTP headers. By default, Nginx includes the version number of the server software in the “Server” header field of HTTP responses. However, this information can be used by attackers to identify the web server software and to search for vulnerabilities that are specific to that software version. As a result, it is important to hide the Nginx version number from HTTP headers to prevent potential attacks.
There are several methods that can be used to hide the Nginx version number from HTTP headers:
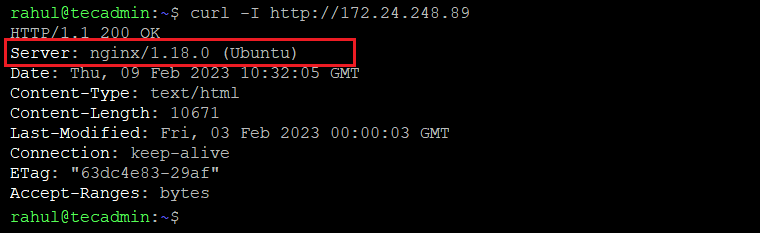
Step 1: Check Current Nginx Headers
You can use the curl command line utility to check HTTP header values on your Nginx web servers. Run the command as below:
curl -I http://172.24.248.89
Replace 172.24.248.89 with your web server IP address.
Step 2: Hiding the Nginx Version
The simplest way to hide the Nginx version number is to use the “server_tokens” directive in the Nginx configuration file. This directive controls the inclusion of the Nginx version number in the “Server” header field. By setting the “server_tokens” directive to “off”, Nginx will not include the version number in the “Server” header field. For example:
1 2 3 4 | server { server_tokens off; # ... } |
Regardless of the method used, hiding the Nginx version number from HTTP headers is an important step in enhancing the security of your web server. By hiding the Nginx version number, you can prevent attackers from using it to identify vulnerabilities in your web server software.
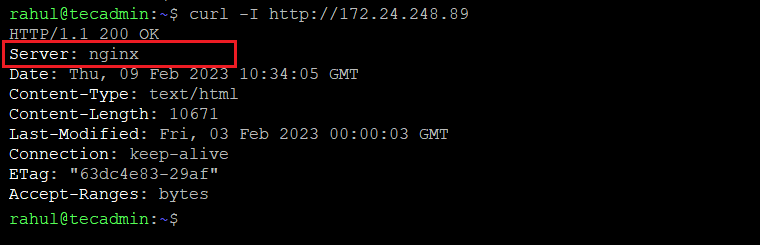
Step 3: Verify Nginx Headers
After making necessary changes, restart Nginx service and again check for HTTP headers.
curl -I http://172.24.248.89
You will see that Nginx version is hidden now.
Conclusion
In conclusion, hiding the Nginx version number from HTTP headers is a simple but effective way to improve the security of your web server. There are several methods that can be used to hide the version number, including using the “server_tokens” directive, modifying the Nginx source code, or using a custom Nginx module. Regardless of the method used, it is important to take the necessary steps to hide the Nginx version number to prevent potential attacks against your web server.
