Keeping your Ubuntu 24.04 server secure is crucial, especially if it’s exposed to the internet. One common threat is unauthorized access attempts, particularly through SSH. Fail2ban is a powerful tool that can help protect your server by automatically blocking suspicious activity.
In this guide, we’ll walk you through the steps to install and configure Fail2ban on your Ubuntu 24.04 server. This guide is designed for beginners, so we’ll keep everything straightforward and easy to follow.
Step 1: Update Your System
Before installing anything, it’s a good idea to update your system to make sure all your packages are up to date. Open your terminal by pressing Ctrl + Alt + T and enter the following command:
sudo apt update && sudo apt upgrade -y
This command updates your package list and installs the latest versions of the packages installed on your system.
Step 2: Installing Fail2ban
First, you need to install Fail2ban on your Ubuntu 24.04 server. Open your terminal and run the following command:
sudo apt install fail2ban
This command installs Fail2ban on your system. Once the installation is complete, Fail2ban will be ready to configure.
Step 3: Configuring Fail2ban
Fail2ban comes with default settings that work well for most users, but you can customize it to suit your needs. The main configuration file is located at /etc/fail2ban/jail.conf, but it’s better to create a local copy for your custom settings to prevent overwriting during updates. Create a new file called jail.local:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Now, open the jail.local file for editing:
sudo nano /etc/fail2ban/jail.local
Step 4: Securing SSH with Fail2ban
To protect your SSH service, locate the [sshd] section in the jail.local file. Here’s a simple example of how to configure it:
[sshd]
enabled = true
port = ssh
logpath = /var/log/auth.log
maxretry = 3
- enabled = true: Activates monitoring for SSH.
- port = ssh: Specifies the port that SSH listens to (usually 22).
- logpath = /var/log/auth.log: Points to the log file where SSH logs are stored.
- maxretry = 3: Sets the number of allowed failed login attempts before banning the IP.
Save the file and exit the editor (in nano, press CTRL + X, then Y, and Enter).
Step 5: Restarting Fail2ban
After making changes, restart Fail2ban to apply the new settings:
sudo systemctl restart fail2ban
You can check the status of Fail2ban to ensure it’s running correctly:
sudo systemctl status fail2ban
Step 6: Monitoring Fail2ban
To see which IP addresses are currently banned, use the following command:
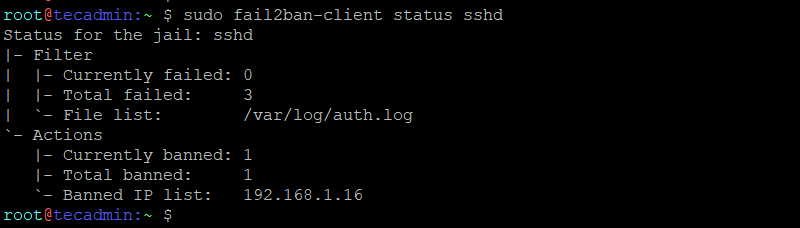
sudo fail2ban-client status sshd
This command shows the number of currently banned IPs and other related information.
Conclusion
By following this guide, you’ve installed and configured Fail2ban on your Ubuntu 24.04 server, enhancing its security against unauthorized SSH access. Fail2ban is a simple yet effective way to protect your server by automatically banning malicious IP addresses after a set number of failed login attempts. With these steps, you can feel more confident in your server’s defenses, knowing that Fail2ban is working in the background to keep it secure.
