Apache HTTP web server is one of the widely used web servers especially on Linux distributions which is a free, cross-platform used by a vast number of websites on the internet. Apache webserver uses HTTP to process the request and entertain web information. Apache has tons of useful features and its functionality can be enhanced with extra modules. It also allows programmers to publish their work on the internet.
So, in this article, we will discuss the installation of the Apache web server and how to secure it after installation on Debian 11.
Requirements
Before installation, you must be logged into the Debian System with access to all sudo privileges. We also recommend completing the initial server setup on newly install Debian 11 systems.
Step 1 – Installing Apache on Debian
The latest version of Apache packages is available under the default Debian 11 repository. So we can directly install it using the packages manager.
After login, open the terminal and update apt cache by below mentioned command:
sudo apt update
After updating of apt cache, now install the Apache2 on your Debian 11 Bullseye by the command:
sudo apt install apache2
Press “y” for any confirmation prompted by the installer.
Once the installation process completed. Verify the installed Apache version by running the following command:
apache2 -v
Output:Server version: Apache/2.4.48 (Debian) Server built: 2021-08-12T11:51:47
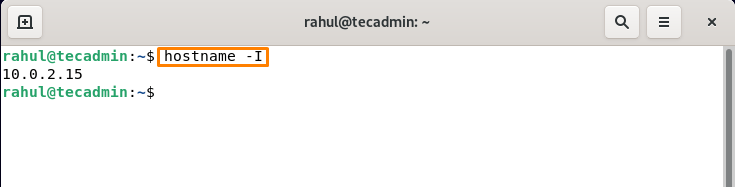
Another way to verify the installation of Apache is by accessing the Apache2 default page using your Server’s IP Address or hostname. If you don’t know your hostname then run the below-mentioned command first:
hostname -I
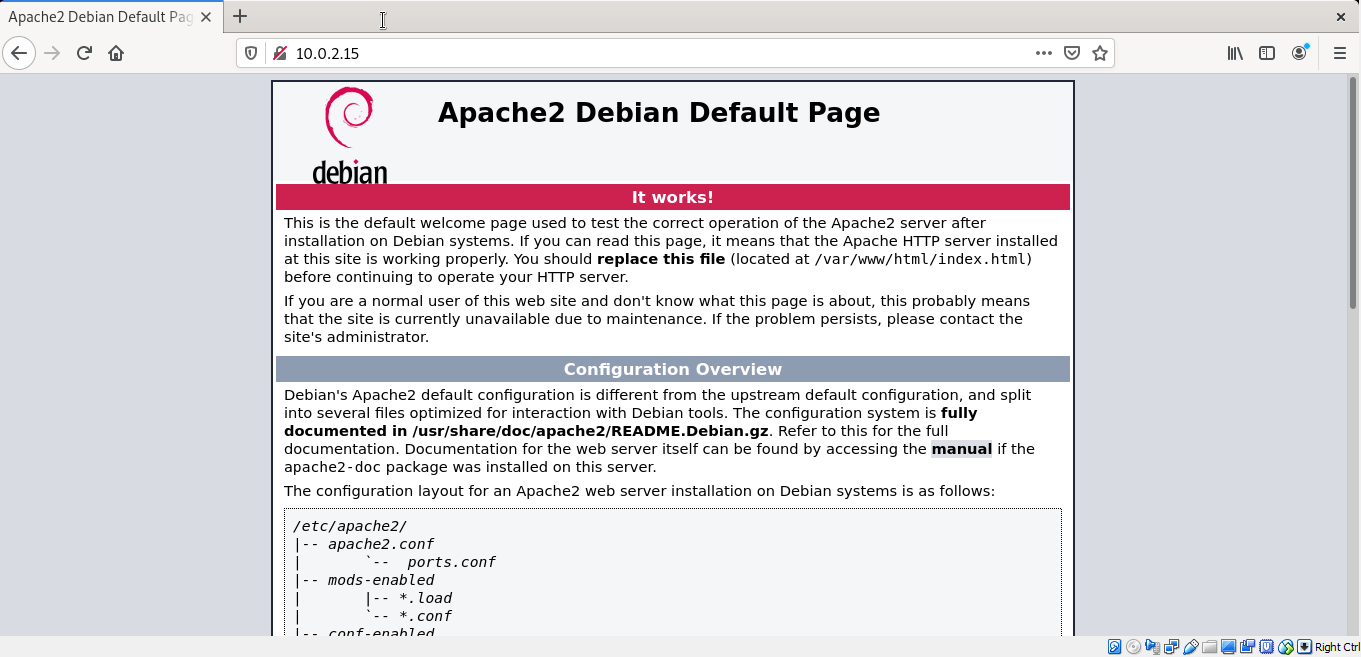
Enter your Server’s hostname or IP address in the URL bar of the browser and press Enter, Apache2 Debian Default page will open as shown below:
Step 2 – Managing the Apache Service
After successful installation, Apache service can be managed using “systemctl” commands, run the below-mentioned command to check the status of the server:
sudo systemctl status apache2.service
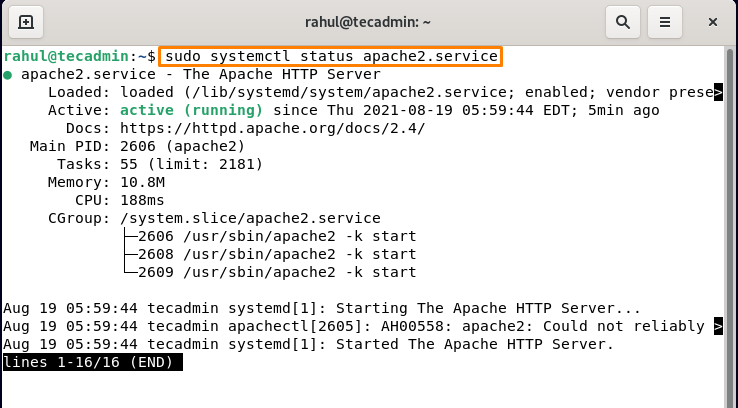
Press “q” to quit. Few commands to manage Apache Service in Debian 11 are:
To start the server use the command:
sudo systemctl start apache2.service
Similarly, to stop service, replace start with a stop in the above command:
sudo systemctl stop apache2.service
The service can be restarted using:
sudo systemctl restart apache2.service
Step 3 – Configuring Firewall Settings
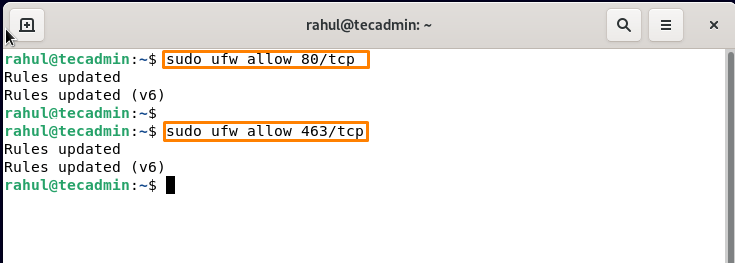
If your system has a firewall, you’ll need to authorize access to certain web ports so that external users can utilize them. Run the below-mentioneds command to allow port 80 (HTTP) and 443 (HTTPS) in the Debian terminal:
sudo ufw allow 80/tcpsudo ufw allow 443/tcp
Now verify by checking the status:
sudo ufw status
if it is not active, to enable its to use:
sudo ufw enable
Step 4 – Creating Virtual Host in Apache
In Apache, virtual hosts allow you to operate numerous websites on a single server. In the Apache web server, we’ll create a virtual host. To accomplish it, we’ll first create a website called sample.com with the server block that comes standard with Apache.
Let’s start by setting up your Apache server’s first virtual host. We’ll use the sample domain as “sample.com”, but you can name it according to your preference:
sudo mkdir -p /var/www/sample.com
Now change the permissions and owner by below-mentioned command:
sudo chown -R www-data:www-data /var/www/sample.comsudo chmod -R 755 /var/www/sample.com
Running below-mentioned command, to test our testdomain.info site, we’ll now construct an example index page. To accomplish so, we’ll use the nano editor to generate an HTML file that looks like this:
sudo nano /var/www/sample.com/index.html
Insert the below mentioned content into index page and press Ctrl+O to save the file an Ctrl+X to exit the file and return to terminal:
[html]
Congratulations! Your sample.com server succeeded!
[/html]
Running the below-mentioned command in a terminal, we’ll build a virtual host file, which will serve the content of server:
sudo nano /etc/apache2/sites-available/sample.com.conf
A text file will be open, insert the following content:
[apache]
ServerAdmin [email protected]
ServerName sample.com
ServerAlias www.sampe.com
DocumentRoot /var/www/sample.com
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
[/apache]
Press Ctrl+O to save the file and Ctrl+X to exit the file and return to the terminal.
Step 5 – Enabling the Domain Configuration
Run the following command to turn on the virtual host file:
sudo a2ensite sample.com.conf
Disable the default Apache Configuration by running below mentioned command:
sudo a2dissite 000-default.conf
New changes to Apache are made applicable by running below mentioned command:
sudo systemctl restart apache2
Step 6 – Resolve Hostname Error
Now, we have to check our configuration for any syntax error, for testing configuration run the below-mentioned command:
sudo apache2ctl configtest
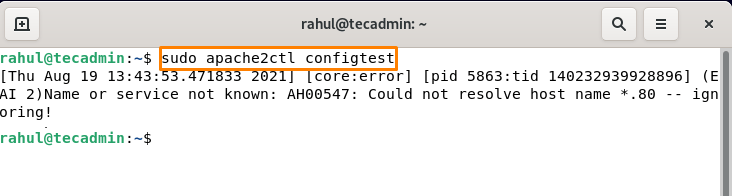
This will cause an error but don’t worry we will resolve this. Create a new configuration “servername.conf” and edit in a text editor:
sudo nano /etc/apache2/conf-avaialable/servername.conf
Now insert the following content into the file:
ServerName sample.com
Press Ctrl+O to save the file and Ctrl+X to exit the file. Make sure to change “sample.com” with your actual domain name. Now to enable the conf server name run the below-mentioned command:
sudo a2enconf servername
Now again run the above command to test configuration:
sudo apache2ctl configtest
You will see that the hostname error is resolved now.
Step 7 – How to secure Apache2 on Debian 11
To secure the Apache server, edit the “security.conf” file, run the below-mentioned command to open the file:
sudo nano /etc/apache2/conf-enabled/security.conf
Insert or update the below content into the file:
[apache]
ServerTokens Prod
ServerSignature Off
TraceEnable Off
Header always append X-Frame-Options SAMEORIGIN
Header always set X-XSS-Protection: “1; mode=block”
Header always set X-Content-Type-Options: “nosniff”
Header always set Strict-Transport-Security “max-age=31536000; includeSubDomains”
Header always edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
[/apache]
Save the file and close it.
Set the server-wide SSLCipherSuite and SSL protocol to use secure ciphers to serve the website by editing ssl.conf file:
sudo nano /etc/apache2/mods-enabled/ssl.conf
Now insert the below-written content into the file and press Ctrl+O to save the file and Ctrl+X to exit the file:
[apache]
SSLProtocol -all +TLSv1.2
SSLCipherSuite HIGH:!aNULL:!MD5
[/apache]
Now run the reload command of Apache to save configuration:
sudo systemctl restart apache2.service
That’s it. You have successfully installed and secured the Apache server.
Conclusion
Apache Web Server is an open-source server used by many websites on the internet and allows developers to publish their work on the internet. This server is available on all OS but in this article, we discuss its installation on the latest version of Debian (Linux OS) and also tell how to test and secure it after its successful installation. You will be able to successfully install Apache2 on Debian 11 Bullseye and configure the server after going through this guide.

3 Comments
1. There are misspellings in the commands you ask readers to paste into their terminals, e.g., ‘sudo nano /etc/apache2/conf-avaialable/servername.conf ‘. I was able to work around them.
2. You provide no explanation for how a reader can determine whether a server has a firewall or not and, hence, whether a reader needs to go through Step 3 or not.
3. I was able to follow the instructions and get apache2 web service up and running through Step 6. However, you provide no explanation as to how security is enhanced by going through Step 7. And, in any event, after completing Step 7 I was unable to restart the service.
—
$ sudo systemctl reload apache2
Job for apache2.service failed because the control process exited with error code.
See “systemctl status apache2.service” and “journalctl -xe” for details.
—
Diagnosing this failure is beyond my abilities. By going back to the original versions of the security.conf and ssl.conf files, I was eventually able to restart the service.
Same here: trashed. Luckily I practiced in a VM first.
I followed your guide completely, and just when I thought it is going to work (finallly – after weeks of trying to get this right), your instructions broke apache2 (with Invalid command ‘SSLProtocol’, perhaps misspelled or defined by a module not included in the server’. Now apache2 just do not run anymore.
I am now going to wipe the installion, and try another instructional website