Kubernetes is a powerful and widely adopted container orchestration platform that automates the deployment, scaling, and management of containerized applications.…
Two-factor authentication (2FA) is a security measure that’s designed to provide an additional layer of protection for your online accounts.…
Squid is a versatile tool that serves as both a proxy server and a web cache system. It helps speed…
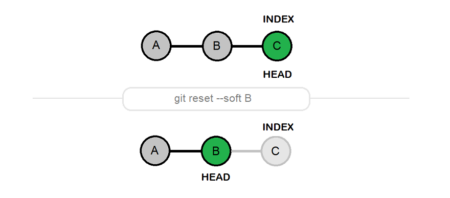
In the realm of software development, version control is paramount. Among the various version control systems available, Git has emerged…
In the continually evolving world of cybersecurity, understanding various types of threats is the first step in protecting yourself or…
A Man-in-the-Middle (MITM) attack is a common cyber-security threat that can have severe consequences if not properly addressed. In this…
Reverse Address Resolution Protocol (RARP) is a protocol used in computer networking, with the primary role of translating physical network…
Git is a widely-used version control system that allows developers to manage and track the changes made to files in…
Git is one of the most popular Version Control Systems (VCS) currently in use, and it provides a wide range…
Git, the popular distributed version control system, introduces a unique feature in its workflow known as the “staging area” or…