Securing your SSH server is important to keep your system safe from unauthorized access. One of the best tools to protect your SSH server is Fail2Ban. It monitors your server logs and automatically blocks IP addresses that show signs of malicious activity, like too many failed login attempts. In this article, we’ll guide you through securing your SSH server in 5 easy steps using Fail2Ban on Debian and RHEL-based systems.
Step 1: Install Fail2Ban
First, you need to install Fail2Ban on your server.
- For Debian-based systems (like Ubuntu):
Open your terminal and run the following command:
sudo apt updatesudo apt install fail2ban -y - For RHEL-based systems (like CentOS, Fedora):
Open your terminal and run the following command:
sudo yum install epel-release -ysudo yum install fail2ban -y
This will install Fail2Ban on your server.
Step 2: Configure Fail2Ban for SSH
After installing Fail2Ban, you need to configure it to protect your SSH server.
1. Create a Local Configuration File:
Fail2Ban uses a configuration file called jail.conf. Instead of editing this file directly, it’s better to create a copy called jail.local to avoid losing your settings when Fail2Ban is updated.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
2. Edit the jail.local File:
Open the jail.local file for editing:
sudo nano /etc/fail2ban/jail.local
Scroll down to find the [sshd] section. Here, you’ll set the rules for protecting your SSH server. Make sure the following lines are present and uncommented:
[sshd]
enabled = true
port = ssh
logpath = %(sshd_log)s
maxretry = 5
enabled = true: This enables Fail2Ban for SSH.port = ssh: This specifies the SSH port (default is 22).logpath = %(sshd_log)s: This is the path to the SSH logs.maxretry = 5: This sets the maximum number of failed attempts before an IP is banned.
Save and exit the editor (in nano, press CTRL + X, then Y, and Enter).
Step 3: Start and Enable Fail2Ban
Now that you’ve configured Fail2Ban, you need to start it and make sure it runs automatically on boot.
sudo systemctl start fail2bansudo systemctl enable fail2ban
This will start Fail2Ban and ensure it runs every time your server boots up.
Step 4: Check Fail2Ban Status
After starting Fail2Ban, it’s a good idea to check its status to make sure it’s running properly.
sudo fail2ban-client status
This command will show you the status of Fail2Ban, including which jails (rules) are active.
To check the SSH jail specifically, run:
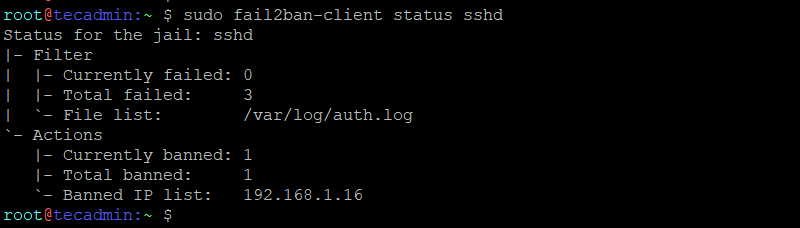
sudo fail2ban-client status sshd
This will show you the number of currently banned IPs and other details.
Step 5: Unban an IP (If Needed)
Sometimes, a legitimate user might get banned accidentally. If this happens, you can unban their IP address.
To unban an IP, use this command:
sudo fail2ban-client set sshd unbanip <IP_ADDRESS>
Replace <IP_ADDRESS> with the actual IP you want to unban.
Conclusion
By following these 5 simple steps, you’ve secured your SSH server with Fail2Ban. Now, your server is better protected against brute-force attacks. Fail2Ban will automatically block suspicious IPs, keeping your server safe from unauthorized access. Make sure to monitor Fail2Ban regularly to ensure it’s working correctly and adjust the settings as needed to suit your security requirements.
