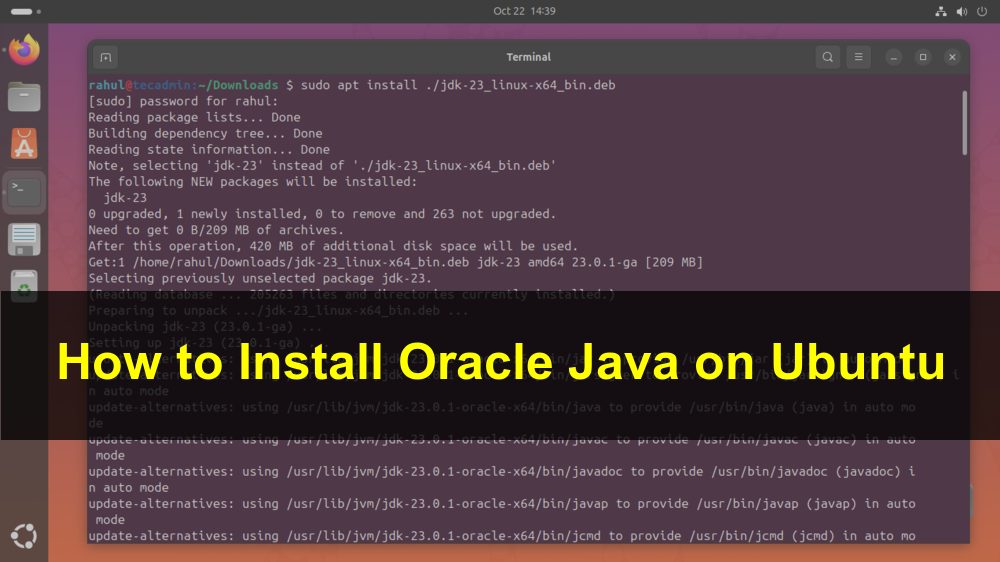
Oracle Java 23 has been released for the Java SE platform. Since this is a long-term support (LTS) version, it will be supported until March 2025. It includes many improvements and bug fixes. If you are using a workstation, you should consider upgrading to this version. Production users should upgrade only after making sure all their applications are compatible. This blog post will help you install Oracle Java 23 on Ubuntu 24.04 LTS, 22.04 LTS, 20.04 LTS, and 18.04 LTS systems using the official Debian file. Follow the steps below to install Java on the Ubuntu command line. Step 1:…
Author: Rahul
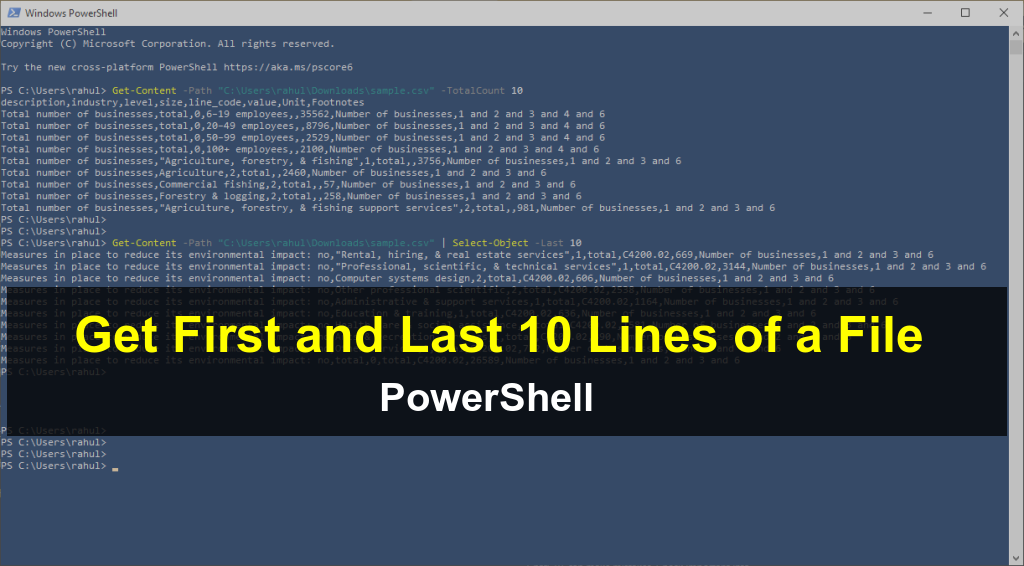
PowerShell provides powerful tools for managing and interacting with files, even when they are large. If you’re working with massive text files, you may only want to view specific portions, such as the first or last few lines, to avoid loading the entire file into memory. In this article, we will explore how to efficiently retrieve the first and last 10 lines of a file using simple PowerShell commands. Fetching the First 10 Lines of a File To extract the first 10 lines of a large file, PowerShell’s Get-Content cmdlet can be used with the -TotalCount parameter. This method allows…
If you own a Mac, you might wonder whether it’s running on Apple’s new Apple Silicon chip or an older Intel chip. This is important because it can affect how your Mac performs and what apps it can run. Apple has been switching its Macs to Apple Silicon chips, which are faster and more efficient, but some older models still use Intel processors. In this guide, we’ll show you a simple way to check if your Mac is powered by Apple Silicon or Intel. Don’t worry—it’s easy and only takes a few steps! Apple Silicon or Intel? Steps to Check…
Python is a popular programming language used by developers worldwide. Ubuntu, a widely-used Linux distribution, typically comes with Python pre-installed, but sometimes you may need a specific version. As of now, Python 3.13 is the latest release, and you can install it on Ubuntu using the Deadsnakes PPA (Personal Package Archive). This tutorial will help you to install Python 3.13 on Ubuntu 24.04, 22.04, and 20.04 step by step. Even if you’re new to Ubuntu or Python, you’ll be able to follow along easily. What Is Deadsnakes PPA? The Deadsnakes PPA is a special repository for Ubuntu users that provides…
Docker service creates many logs on your system. Each Docker container makes its own log file, and the Docker service also creates its own. If your system is running out of disk space and you see Docker container logs taking up a lot of space, this tutorial will show you how to find and clear them. You don’t need to stop the Docker container to clear its log files. This guide will help you clear a Docker container’s log file, freeing up disk space and improving system performance. Regularly managing log files is essential, especially when running multiple containers that…
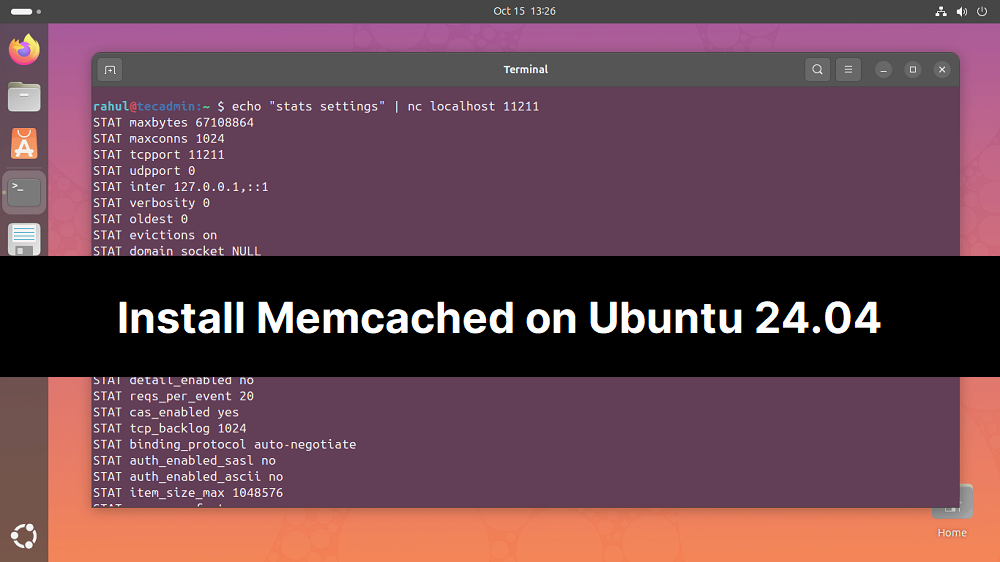
Memcache is the powerful in memory database server widely used for high performance data storage. It stored the object in format of key-value pairs, which is very suitable format for string objects. It is widely used for storing sessions in a load balancing environment. Many of the dynamic websites uses Memcahe for caching object to achieve and high throughput This article will help you to install and configure Memcached server on Ubuntu 24.04 LTS systems. Step 1: Install Memcached First of all, update Apt package cache on your system then install Memcached service on your system. Execute below commands from…
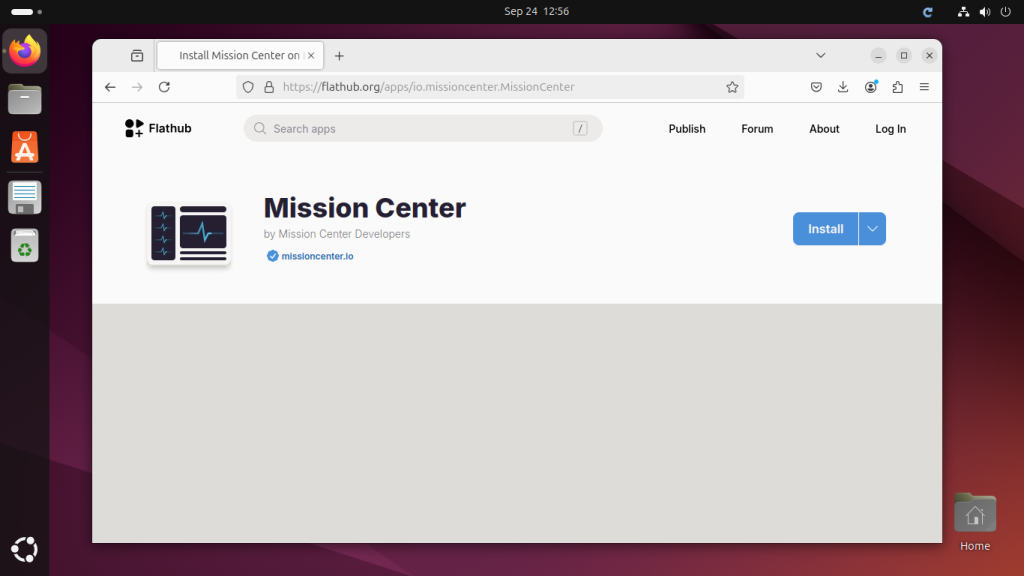
Mission Center is an ultimate system monitoring application build for Linux Desktop operating systems. This will provide you an ultimate look and feel something like Windows task manager. The Mission center application provides you details statics for real-time CPU, Memory utilization. Manage running applications and services on your system. This tutorial will guide you through installation of Mission Center application on your Ubuntu desktop systems. Step 1: Download Installation File Mission Center application provide flatpak file for the installation on Linux systems. Go to the flathub Mission Center download page and click the install button located on page. This will…
C programming provides several ways to swap two variables, meaning we exchange their values with each other. Which helps you better to work with the variables in a programming language. This article will show you three methods to swap variables: using a temporary variable, without using a temporary variable, and using pointers. Along with each method, we’ll also walk through a step-by-step dry run of the code to make it easy to understand. Method 1: Using a Temporary Variable This is the simplest way to swap two variables. We use a third variable, often called “temp,” to hold one value…
Microsoft Edge is cross-platform browser developed by Microsoft in year 2015. Initially it was build on their own propriety browser engine and Chakra JavaScript engine. This browser protects from malicious websites and downloading files better than any other browsers. This article will help you to install Microsoft Edge browser on Ubuntu system using graphical user interface as well as command line interface. Step 1: Download Edge Browser Navigate to the Microsoft Edge browser official Download page. Click the “Download Edge” button showing on screen (User interface is frequently updated, so if you don’t see button search for the .deb file)…
Mission Center is an graphical application used for monitoring system resources. It provide an awesome design for better user experience. This application is written on Rust programming language. To install this on your Linux system using Flatpak file provide on the official site. Download the above file and install on your Linux system. Mission Center’s Features Monitor CPU usage, either overall or by individual threads. View system details like process count, thread count, handle count, uptime, current and base clock speed, and cache sizes. Track how much RAM and Swap memory your system is using. Get a clear breakdown of…