Port Knocking is a technique used to secure connections or port access from unwanted users. Using this technique we maintain one or more previously configured ports closed and these will only be opened using a sequence of requests to a number of ports that wepreviouslyset .
To give an example , if we configure port Knocking access to port 50, this port will only be open when we make requests to the ports 1000,2500,3000 in that order , doing so, once we complete the sequence correctly the firewall will open the port that was previously closed.With this we add another level of security to certain types of connections to our server.
The client can perform the port knocking using Nmap, Telnet, or a tool for these purposes.
Let’s secure SSH connections using this method on a server running Linux CentOS . Follow the below steps as root.
Install Prerequisites
Install the libpcap library packages as requirment of Knock-server
# yum install libpcap*
Install Knock Server Package
Download and install knock-server rpm package
# wget http://li.nux.ro/download/nux/misc/el6/i386/knock-server-0.5-7.el6.nux.i686.rpm # rpm -ivh knock-server-0.5-7.el6.nux.i686.rpm
Before setting up the Knockd daemon, we must create an iptable rule the drops all connections to the SSH port , in this case we ‘ll use the default (22).
# iptables -A INPUT -p tcp --dport 22 -j DROP # service iptables save
[NOTE: Do not use below command it you are connected with SSH to server, It will drop your current connection]
OK ,we can now configure our knockd daemon so that out SSH port opens after a correct port knocking Sequence. Edit knockd configuration file add following values
# vi /etc/knockd.conf
[options]
logfile = /var/log/knockd.log
[openSSH]
sequence = 5040,6010,6500
seq_timeout = 30
tcpflags = syn
Start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
[closeSSH]
sequence = 4040,5050,8080
seq_timeout = 30
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Save the file and Quit (:wq!)
Finally start the Knockd service
# service knockd start
How to Use Port Port Knowcking
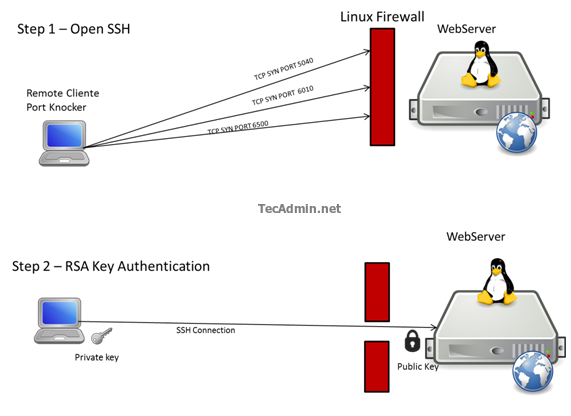
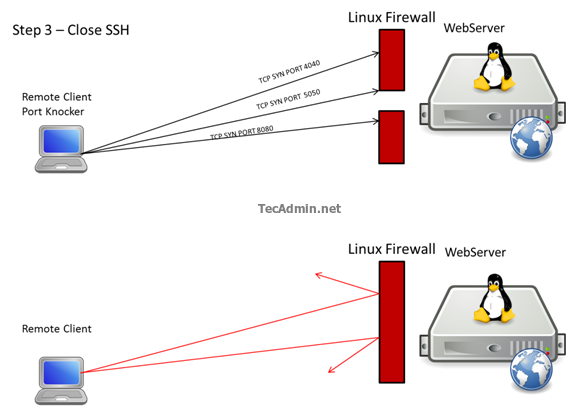
Here to open the SSH port we will knock ports 5040,6010,6500 and when the sequence is completed correctly it will run a command that will add a rule in the firewall to allow the connection to our Linux Server via port 22 . We have another directive to close the port,Knocking ports 4040,5050,8080 it will run a command that will remove the Firewall rule that allowed us to do the connection via SSH.
To Knock the ports you can use the tool Nmap or Telnet as follow. For this example we use nmap.
To Open the SSH connection
# nmap -p 5040 SERVER-IP # nmap -p 6010 SERVER-IP # nmap –p 6500 SERVER-IP
To close the connection
# nmap -p 4040 SERVER-IP # nmap -p 5050 SERVER-IP # nmap -p 8080 SERVER-IP
If we see the Knockd log we will have something like this
# tail /var/log/knockd.log [2014-04-10 05:20] 192.168.1.184: openSSH: Stage 1 [2014-04-10 05:21] 192.168.1.184: openSSH: Stage 2 [2014-04-10 05:21] 192.168.1.184: openSSH: Stage 3 [2014-04-10 05:21] 192.168.1.184: openSSH: OPEN SESAME [2014-04-10 05:21] openSSH: running command: /sbin/iptables -I INPUT -s 192.168.1.184 -p tcp --dport 22 -j ACCEPT
I’m going to show a little more graphical .
This is a brief representation of the process including authentication with RSA keys.
Here we have our remote connections with a good level of security and combine with RSA authentication we hardened the connection even more. We can use this method to secure any type of connections to our Linux Server. To read more about visit http://www.zeroflux.org/projects/knock


2 Comments
hi, i did as you said, but that doesn’t work.
but i deleted the iptable rule, and did the steps again and add the ip rule at the end, and that worked , thanks :)))
Don’t forget to configure your server to start knockd when it boots:
chkconfig –level 2345 knockd on