In real-life terms, Port forwarding is like telling the delivery driver where to go in a large apartment complex. Normally, the complex’s main door is locked to outsiders. But if someone from inside expects a delivery, they can tell the security guard to let the driver in and direct them to the specific apartment.
Similarly, in computer networks, port forwarding lets someone from outside access a service inside a private network that they usually wouldn’t be able to reach. This is useful when you want to let people outside your network use a web server, play games on your game server, or access other types of services you set up.
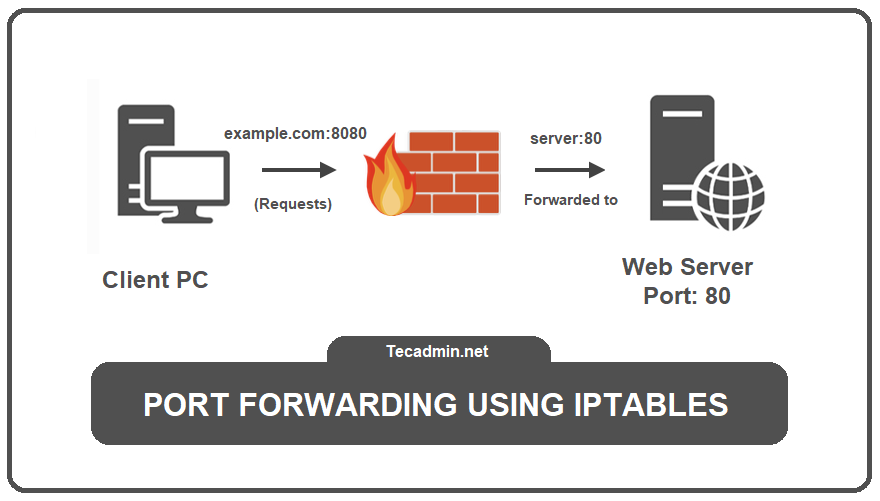
Linux operating systems, such as Ubuntu, CentOS, and Debian, use a tool called “iptables” to set up port forwarding. Iptables is a program that lets you set rules for how data packets are allowed to move through your computer’s firewall, which helps keep your network secure. These rules are sorted into different groups based on what they do.
In this tutorial, we’ll show you how to set up port forwarding using iptables on a Linux system.
Prerequisites
- A Linux machine with root or sudo access.
- The iptables package should be installed. If not, you can install it using the package manager for your distribution (like apt, dnf, or yum).
A Step-by-Step Guide
Step 1: Install Iptables
Firstly, make sure the iptables pacakges are installed on your Linux machine. If it is not installed, install it using the default package manager of your Linux distribution.
- For Debian and Ubuntu, use the following command:
sudo apt updatesudo apt install iptables - For CentOS, Fedora or RHEL, use:
sudo dnf install iptables
Step 2: Check Existing Rules
Before you start modifying your iptables rules, it’s always a good idea to take a look at the current rules.
sudo iptables -L -v -n
The -L flag lists the rules, -v shows more verbose information, and -n displays IP addresses and port numbers in numerical format.
Step 3: Enable IP Forwarding
To allow forwarding at the kernel level, we need to enable IP forwarding.
Edit the /etc/sysctl.conf file:
sudo nano /etc/sysctl.conf
Add or uncomment the following line:
1 | net.ipv4.ip_forward=1 |
To apply the changes, run:
sudo sysctl -p
This will make sure IP forwarding is enabled on boot.
Step 4: Configure the Forwarding Rule
To forward traffic from one port to another, use the following command:
sudo iptables -t nat -A PREROUTING -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:80
Replace 8080 with the port number on which your system receives traffic, 192.168.1.100 with the IP address of the device to which you want to forward the traffic, and 80 with the port number on the destination device.
Step 5: Masquerade the IP
Finally, to ensure the correct routing of return packets, you should use the MASQUERADE target, which will masquerade the IP address of the incoming packets with the IP address of the outgoing network interface.
sudo iptables -t nat -A POSTROUTING -j MASQUERADE
Step 6: Save the Changes
To save the changes permanently so that they persist after a reboot, you will need to save these rules.
In Ubuntu, you can use the iptables-persistent package. Install it using:
sudo apt install iptables-persistent
During the installation, it will ask if you want to save existing iptables rules. Select Yes for both IPv4 and IPv6 rules.
For CentOS, Fedora or RHEL, you can use:
sudo service iptables save
This will save your rules to /etc/sysconfig/iptables.
Step 7: Verify the Configuration
You can verify if the port forwarding works by connecting to the source port from another device. You can use a tool like nc, telnet, or curl to verify this.
Remember to check if any existing firewall rules or security groups may be blocking access to the source or destination ports.
Conclusion
Iptables is a powerful tool that allows Linux administrators to configure specific rules for packet forwarding and other firewall-related tasks. By following the steps outlined in this article, you can successfully set up port forwarding using iptables on a Linux system. Always remember to verify your rules and ensure your configurations align with your network security policies.
