Cross-Site Scripting, commonly known as XSS, is a prevalent form of client-side attack in the realm of web security. It involves the injection of malicious scripts into a web application. Once injected, these scripts use the compromised application as a vehicle to reach other users’ browsers. When these scripts are executed by the browser of an unsuspecting user, they are perceived as originating from a trusted source, thus bypassing normal security checks.
Secure Apache from Cross-Site Scripting (XSS)
One effective method to safeguard your Apache web server against XSS attacks is through the implementation of the `X-XSS-Protection header. This approach is both straightforward and robust.
- Editing the Configuration File: Navigate to your Apache configuration file. This file is typically located at
/etc/httpd/conf/httpd.conffor Apache installations on Linux or/etc/apache2/conf-enabled/security.conffor other configurations. - Setting the X-XSS-Protection Header: Add the following line to the configuration file:
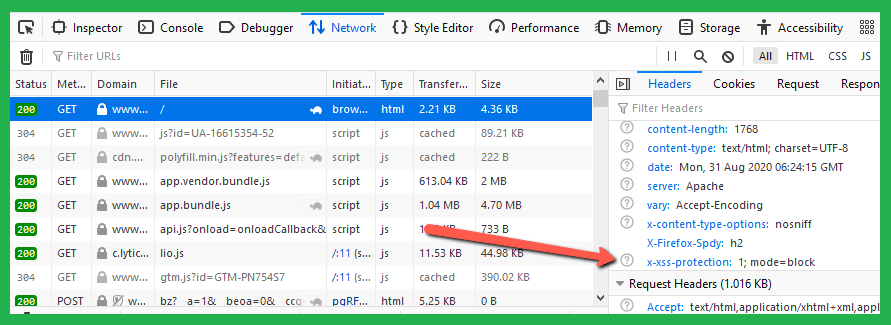
Header always set X-XSS-Protection "1; mode=block"This line of code instructs the server to always set the X-XSS-Protection header. The value “1; mode=block” activates the XSS Filter built into most modern web browsers.
- Saving the Configuration File: After adding the line, save the file and close the editor.
- Effect of the Settings: With these settings enabled, if a cross-site scripting attack is detected by the browser, it will attempt to sanitize the page, neutralizing the malicious script. Furthermore, in more severe cases, it may prevent the rendering of the page altogether to safeguard the user’s data and privacy.
- Restarting Apache: To apply the changes, restart the Apache service. This can typically be done using a command like
sudo systemctl restart apache2on most Linux distributions.sudo systemctl restart apache2
Verifying XSS Protection Settings
To check the effectiveness of your XSS protection settings, navigate to your website using any web browser. Once there, press F11 to access the browser’s ‘Inspect Element’ tool. This will allow you to inspect the headers for the web requests. Look for the header values related to XSS protection, as illustrated in the image below.
Conclusion
By setting the X-XSS-Protection header in your Apache configuration, you add a significant layer of defense against XSS attacks. This measure, in conjunction with other security practices, can greatly enhance the safety and integrity of your web applications and the data they handle. Remember, the world of web security is ever-evolving, and staying abreast of the latest threats and countermeasures is key to maintaining a secure web environment.

1 Comment
Non-standard: This feature is not standardized.
Deprecated: This feature is no longer recommended
Warning: Even though this feature can protect users of older web browsers that don’t support CSP, in some cases, X-XSS-Protection can create XSS vulnerabilities in otherwise safe websites.