Internet Control Message Protocol (ICMP) represents a crucial element within the Internet Protocol Suite, utilized by various network devices to convey error messages and operational details. Such details can indicate the absence of a requested service or an inability to reach a host or router. Essentially, ICMP serves as a messenger of network communication errors and operational statuses.
First outlined in RFC 792 by the Internet Engineering Task Force (IETF), ICMP is designated as protocol number 1 within the Internet Protocol Suite, accompanying the primary transport protocols – TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Structure of ICMP
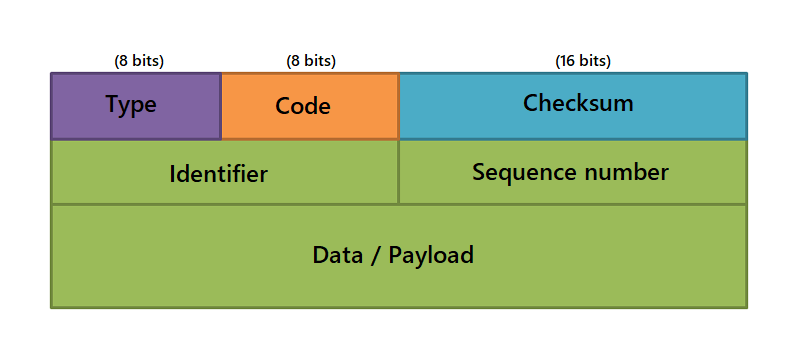
An ICMP message has a specific structure. It begins with an 8-byte header followed by a variable-sized data section. The header includes a type field (8 bits), a code field (8 bits), and a checksum field (16 bits). The remaining 32 bits are used for different purposes based on the type and code of the message.
- Type: This field indicates the type of ICMP message. For instance, an ICMP Echo Request, which is used in the PING utility, has a type of 8, and an ICMP Echo Reply has a type of 0.
- Code: This field provides further information about the message type. For example, with a Destination Unreachable message (type 3), different codes specify whether the destination network is unreachable, the destination host is unreachable, the destination protocol is unreachable, etc.
- Checksum: This field is used to ensure the integrity of the ICMP message. It is computed as the 16-bit one’s complement of the one’s complement sum of the ICMP message starting with the Type field.
The data that follows the header varies based on the type and code of the message. For example, in an Echo Request or Echo Reply, it typically includes a sequence number and some amount of arbitrary data.
Role of ICMP
ICMP plays a crucial role in the management and operation of internet networks. Below are some key functions:
- Error Reporting: ICMP allows devices to send error messages back to the source of a problematic packet, typically when a packet cannot be processed properly. It supports numerous error messages, including Destination Unreachable, Source Quench, Time Exceeded, and Redirect.
- Operational Information: ICMP messages are also used to share operational information about the state of the network. For example, an ICMP Echo Request (commonly known as a “ping”) can be used to check if a specific destination is reachable and how long packets take to travel to that destination and back.
- Network Troubleshooting: ICMP is invaluable for diagnosing network problems. Tools like “ping” and “traceroute” rely on ICMP messages to check network connectivity and find the paths packets take through a network, respectively.
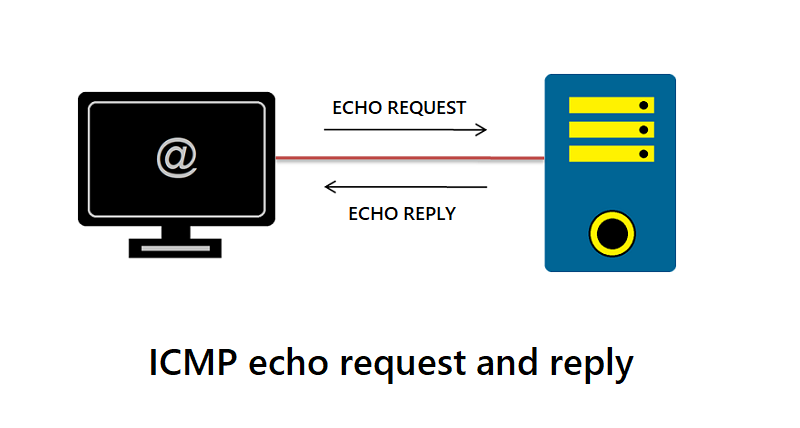
ICMP Echo Request and Reply
The ICMP Echo Request and Echo Reply messages are an integral part of the ICMP protocol and are widely used for diagnostic purposes, primarily through the Ping utility.
ICMP Echo Request
An ICMP Echo Request is a message sent by a device that wants to “ping” or query the reachability and latency to another device on an IP network. Here’s the process:
- A device intending to ping another device creates an ICMP Echo Request message. The message includes a header and some amount of arbitrary data.
- The message is then encapsulated in an IP packet. The source IP address is set to the IP address of the device sending the request, and the destination IP address is set to the IP address of the device to be pinged.
- The packet is then sent out on the network.
ICMP Echo Reply
Once an ICMP Echo Request is received, the following steps are followed:
- Upon receiving an ICMP Echo Request message, the target device creates an ICMP Echo Reply message. This message contains the same data as the request message.
- This reply message is encapsulated in an IP packet. This time, the source IP address is set to the IP address of the device sending the reply (i.e., the device that was pinged), and the destination IP address is set to the IP address of the device that sent the Echo Request.
- The Echo Reply packet is then sent back to the original sender.
By measuring the time it takes for an Echo Request to be sent and an Echo Reply to be received, a device can estimate the round-trip time or latency between itself and another device on the network. If no Echo Reply is received within a certain timeframe, the device can assume that the target device is not reachable.
These ICMP messages, thus, facilitate the detection of network connectivity issues, measure latency, and provide a simple mechanism to map network paths.
Security Considerations
ICMP, while invaluable, can also be used maliciously. An attacker can leverage ICMP messages to perform a variety of attacks, such as ICMP flood attacks (where an attacker overwhelms a network with ICMP traffic) or ICMP tunneling (where an attacker covertly sends data encapsulated in ICMP packets).
Consequently, network administrators need to configure firewalls and intrusion detection/prevention systems to manage ICMP traffic correctly. This might involve blocking certain types of ICMP messages entirely or rate-limiting ICMP traffic to prevent flood attacks.
Conclusion
The Internet Control Message Protocol (ICMP) is a fundamental component of the internet protocol suite, crucial for error handling and network diagnostics. Despite its potential misuse in network attacks, its benefits in maintaining and managing the health of internet networks are indispensable. By understanding its function and proper handling, network administrators can optimize its benefits while minimizing its potential risks.